- Security Blog
- By Eduard Kovacs
- September 13th, 2012

Page: Critical Limited Edition Malware Targets Defense Industry
The attack starts with a legitimate-looking PDF file
- Security Blog
- By Eduard Kovacs
- September 13th, 2012
![Researchers Demonstrate CRIME Attack Against TLS Protocol [Video] Researchers Demonstrate CRIME Attack Against TLS Protocol [Video]](https://news-cdn.softpedia.com/images/news2/Researchers-Demonstrate-CRIME-Attack-Against-TLS-Protocol-Video-1.png)
Researchers Demonstrate CRIME Attack Against TLS Protocol [Video]
The experts who presented the BEAST attack return with a new discovery
- Security Fixes and Improvements
- By Eduard Kovacs
- September 12th, 2012

Poor Protocol Implementation Makes EMV Chip-and-PIN Cards Vulnerable
Cambridge researchers may have come up with an explanation for "phantom" withdrawals
- Security Blog
- By Eduard Kovacs
- September 11th, 2012

Shamoon Created by American-Hater Amateur Developers
Kaspersky experts have further analyzed the malware
- Virus alerts
- By Eduard Kovacs
- September 11th, 2012

Buggy Malware Found to Target French Nuclear Power Company
Norman researchers are uncertain if it's a flawed attack or simply a way to confuse them
- Security Blog
- By Eduard Kovacs
- September 10th, 2012

DarkShell Keylogger Comes as Windows Help File
Innocent-looking files can hide dangerous malware
- Security Fixes and Improvements
- By Eduard Kovacs
- August 31st, 2012
Cybercriminals Could Take Phishing to the Next Level by Using URIs
Henning Klevjer analyzes such attacks in his latest research paper
- Security
- By Eduard Kovacs
- August 30th, 2012

Teens Get Bullied Online, but Parents Are Unaware of Their Activities, Study Finds
“The Digital Divide: How the Online Behavior of Teens is Getting Past Parents” released
- Server related
- By Eduard Kovacs
- August 30th, 2012

Fujitsu, eBay and Verizon Team Up for Big Data Working Group
Cloud Security Alliance’s new project has been launched
- Security Fixes and Improvements
- By Eduard Kovacs
- August 30th, 2012
![Experts Demonstrate Hotel Room Lock Hack, Improve Methods [Video] Experts Demonstrate Hotel Room Lock Hack, Improve Methods [Video]](https://news-cdn.softpedia.com/images/news2/Experts-Demonstrate-Hotel-Room-Lock-Hack-Improve-Methods-Video-1.png)
Experts Demonstrate Hotel Room Lock Hack, Improve Methods [Video]
Some of the new gadgets can fit inside an iPhone case
- Virus alerts
- By Eduard Kovacs
- August 29th, 2012

Researchers Unable to Link Mysterious Wiper Malware to Flame
There's not enough evidence to connect it to Duqu and Stuxnet either
- Security Blog
- By Eduard Kovacs
- August 29th, 2012
Shylock Malware Replaces Documents with Shortcuts to Malicious Files
This is possible thanks to a component called DiskSpread
- Security Blog
- By Eduard Kovacs
- August 29th, 2012

Developers Improve Mahdi, Add Fifth Command and Control Server in Canada
150 organizations from all around the world have been targeted so far
- Security
- By Eduard Kovacs
- August 27th, 2012
![Security Overview of Berlin 2012 Campus Party [Video] Security Overview of Berlin 2012 Campus Party [Video]](https://news-cdn.softpedia.com/images/news2/Security-Overview-of-Berlin-2012-Campus-Party-Video-1.png)
Security Overview of Berlin 2012 Campus Party [Video]
The founder of Vulnerability Labs told Softpedia all about the hackathon
- Security
- By Eduard Kovacs
- August 23rd, 2012
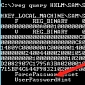
Windows 7 and Windows 8 Registries Reveal Password Hints, Researchers Find
The hints are encrypted, but they’re not difficult to decrypt
- Security Fixes and Improvements
- By Eduard Kovacs
- August 22nd, 2012

Frankenstein: Undetectable Malware Created from Pieces of Common Software
University of Texas researchers show that code from Notepad could be used to build malware
- Virus alerts
- By Eduard Kovacs
- August 21st, 2012

Ransomware: Bad Guys, Good Guys and Untraceable Money Transfer Systems
ESET experts detail the way a ransomware scheme works