- Security Fixes and Improvements
- By Eduard Kovacs
- October 23rd, 2012

Possibilities for Malicious Browser Extensions Are Almost Infinite, Researcher Says
These components can be far more dangerous than what we've seen so far
- Security
- By Eduard Kovacs
- October 22nd, 2012

Many of the Android Apps Using SSL Vulnerable to MITM Attacks, Experts Find
Researchers performed an analysis with the aid of a tool called MalloDroid
- Security Blog
- By Eduard Kovacs
- October 22nd, 2012
Sites of Indian Mobile Operators Idea, Tata and BSNL Contain Serious Vulnerabilities
Security researcher Prashant Uniyal explains why these flaws are so dangerous
- Security
- By Eduard Kovacs
- October 22nd, 2012

Cybercriminals Found to Sell Access to Servers Housed by Fortune 500 Companies
The machines have been compromised because they have weak RDP passwords
- Virus alerts
- By Eduard Kovacs
- October 20th, 2012
.Gov URLs Used to Advertise “Make Money” Scam, over 43,000 Victims Recorded
Symantec experts explain how cybercriminals can pull off such a stunt
- Security Fixes and Improvements
- By Eduard Kovacs
- October 19th, 2012
Experts Develop Malware That’s Capable of Bypassing Antivirus Solutions
Complicated tasks are achieved by utilizing simple methods
- Security Blog
- By Eduard Kovacs
- October 19th, 2012

The DHS Wants to Introduce the Advanced Bottled Liquid Scanner
The agency wants a prototype to be ready in three years
- Virus alerts
- By Eduard Kovacs
- October 19th, 2012

MUSTAN Malware Avoids Infecting Certain Files to Hide Its Presence
Trend Micro experts have analyzed this interesting threat
- Virus alerts
- By Eduard Kovacs
- October 19th, 2012
Fake Lookout Mobile Security Update Steals Files from Android Users
Researchers say that the malware is part of a larger attack
- Virus alerts
- By Eduard Kovacs
- October 18th, 2012
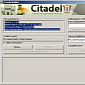
Citadel Trojan Rain Edition Represents Fraud-as-a-Service at Its Best, RSA Says
Some new features have been added, but the price has also gone up
- Security Blog
- By Eduard Kovacs
- October 18th, 2012

Experts: miniFlame Is Similar to PlugX and PoisonIvy, Not a Threat to Regular Users
The malware's capabilities are not so different from the ones of other backdoor threats
- Security Blog
- By Eduard Kovacs
- October 17th, 2012

Hackers Could Hijack Pacemakers and Remotely Deliver Deadly Electric Shocks
Security researcher Barnaby Jack unveiled his findings at the BreakPoint conference
- Virus alerts
- By Eduard Kovacs
- October 17th, 2012

Expert Explains How Facebook Users End Up with Shady Video Links on Their Walls
Security researcher Troy Hunt shows the inner workings of a worm
- Security Fixes and Improvements
- By Eduard Kovacs
- October 17th, 2012

Hackers Can Bypass PayPal’s Token-Based 2FA via the Password Reset Function
Researchers stress that cybercriminals can access the accounts by using spyware
- Security Blog
- By Eduard Kovacs
- October 16th, 2012
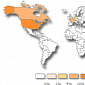
Windows Help Files Used in Attacks Against Industry and Government Sectors
Cybercriminals rely on a cool trick to execute code and install malware
- Security Fixes and Improvements
- By Eduard Kovacs
- October 16th, 2012
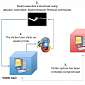
Steam Browser Protocol Flaws Allow Cybercriminals to Execute Malicious Commands
Experts have published a video proof-of-concept to demonstrate their findings
- Apple & Mac Blog
- By Eduard Kovacs
- October 15th, 2012

Multiplatform Jacksbot Malware Steals Minecraft Passwords, Other Information
Intego experts have analyzed a new variant of the Trojan