- Security Fixes and Improvements
- By Eduard Kovacs
- December 10th, 2012

GPS Software Attacks More Dangerous Than Jamming and Spoofing, Experts Say
Carnegie Mellon University researchers have identified new attack vectors
- Security Blog
- By Eduard Kovacs
- December 8th, 2012
Malware Disguised as Trend Micro Product Spreads Bitcoin Miner
These types of threats help cybercriminals make a decent profit
- Security Fixes and Improvements
- By Eduard Kovacs
- December 7th, 2012
Details of Several Critical Vulnerabilities in Maxthon and Avant Browsers Published
Roberto Suggi Liverani has made available technical documentation and videos
- Security Blog
- By Eduard Kovacs
- December 7th, 2012

Necurs Malware Infects over 83,000 Machines in November 2012, Microsoft Says
Experst have thoroughly analyzed this dangerous threat
- Security Blog
- By Eduard Kovacs
- December 7th, 2012

BlackHole Exploit Kit Has Difficulties in Infecting Chrome Users, Experts Say
Unlike Firefox or IE, Google's browser is not so easy to attack
- Security Blog
- By Eduard Kovacs
- December 6th, 2012

Pakistani Hackers Flood Pastebin with Links to Compromised Sites
Websense researchers noticed a spike on November 20
- Hacking News
- By Eduard Kovacs
- December 6th, 2012

Eurograbber Campaign Steals over €35 Million from European Bank Customers
30,000 accounts belonging to companies and individuals have been breached
- Security Blog
- By Eduard Kovacs
- December 5th, 2012
Users Advised to Disable Smart Card for Protection Against Shylock Malware
This method is used to trick the threat into thinking that it's being analyzed
- Security Fixes and Improvements
- By Eduard Kovacs
- December 4th, 2012

DefCamp 2012: Flaws in Mobile Networks Allow Users to Surf the Web for Free
Security researcher Bogdan Alecu has demonstrated how this can be done
- Security Fixes and Improvements
- By Eduard Kovacs
- December 4th, 2012

Hackers Can Use Twitter SMS Vulnerability to Post on Users’ Behalves, Expert Finds (Updated)
The attack relies on spoofing the number from which the message originates
- Security Blog
- By Eduard Kovacs
- December 4th, 2012

ZeuS and Changeup Malware Help Each Other Spread, Experts Find
Symantec experts have located the source of the Changeup worm
- Security Fixes and Improvements
- By Eduard Kovacs
- December 4th, 2012
Tumblr Worm Might Have Leveraged Stored XSS Vulnerability, Expert Says
According to Janne Ahlberg, the issue is still not fixed
- Security Blog
- By Eduard Kovacs
- December 3rd, 2012
Sophos Releases Technical Paper on BlackHole Exploit Kit
Researchers believe that the malicious element has been developed in Russia
- Security Fixes and Improvements
- By Eduard Kovacs
- December 1st, 2012

DefCamp 2012: Bypassing Security Tokens for Exploitation of Rounding Vulnerabilities
Presentation of a clever device developed by Adrian Furtuna
- Security Blog
- By Eduard Kovacs
- November 28th, 2012
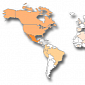
New Version of Changeup Malware Found Targeting India, Mexico, Other Countries
Symantec experts are currently monitoring the updated variant
- Security Blog
- By Eduard Kovacs
- November 27th, 2012
Cybercriminals Sell Apache-Based iFrame Injection Module for $1,000 (€800)
Some clever techniques are deployed to make the tool stealthy
- Security Blog
- By Eduard Kovacs
- November 27th, 2012
PlugX RAT Developers Release New Version, Become More Confident
Kaspersky experts have found that the error logging function has been removed