- Security Blog
- By Eduard Kovacs
- November 5th, 2012

Experts Find DOM XSS Flaw in “+1” Button of Google Plus - Video
The vulnerability was found with the aid of a tool called DOMinatorPro
- Security Blog
- By Eduard Kovacs
- November 5th, 2012
Researchers Find Smishing Vulnerability in Android, All Versions Affected – Video
Google is already working on addressing the security hole
- Security Blog
- By Eduard Kovacs
- November 2nd, 2012
“China Hacked by Anonymous” YouTube Video Promotes Facebook Hack Tool
The application hides an information-stealing Trojan
- Security Blog
- By Eduard Kovacs
- November 1st, 2012
Cybercriminals Continue to Improve Skype-Spreading Malware
New languages and download locations have been added
- Security Blog
- By Eduard Kovacs
- October 31st, 2012

Huawei Wants to Ask German Security Researcher for Help in Patching Up Devices
Felix Lindner has identified a number of vulnerabilities in the company's devices
- Hacking News
- By Eduard Kovacs
- October 31st, 2012

Georgian CERT Uses Malware to Identify and Photograph Russian Hacker
The man is believed to be responsible for the Georbot botnet
- Virus alerts
- By Eduard Kovacs
- October 30th, 2012

Security Experts Warn About Android Apps Bundled with sellAring Ads
Aggressive ad platforms can ruin a developer's reputation
- Security Blog
- By Eduard Kovacs
- October 30th, 2012
Malware Responsible for Israeli Police Department Shutdown Analyzed
Trend Micro experts have obtained a sample of the email designed to spread a RAT
- Virus alerts
- By Eduard Kovacs
- October 30th, 2012

Malware Uses Mouse Actions, “Sleep” Mode to Evade Detection
Researchers explain how malicious elements hide from threat analysis systems
- Virus alerts
- By Eduard Kovacs
- October 30th, 2012
Gamarue Malware Hides in Hotel Booking Confirmations Sent to German Users
Trend Micro experts have analyzed this particular spam campaign
- Security
- By Eduard Kovacs
- October 27th, 2012
Researchers Highlight the Pros and Cons of Windows 8 Security Systems
Windows Defender, UEFI and ELAM analyzed by Trend Micro experts
- Security Blog
- By Eduard Kovacs
- October 26th, 2012
Security Experts: We Hope Windows 8 Is Immune to Old Exploitation Techniques
FireEye researchers say protocol standards must be strictly enforced
- Security
- By Eduard Kovacs
- October 26th, 2012
Faulty SSL Certificate Validation Exposes Apps to MitM Attacks, Researchers Find
Amazon libraries, PayPal's merchant SDK, and various shopping carts are affected
- Security
- By Eduard Kovacs
- October 25th, 2012

RSA, AMD, Intel, Lockheed Martin and Honeywell Team Up for Cyber Security Alliance
The big players hope they can get the private sector and the government to work together
- Security Fixes and Improvements
- By Eduard Kovacs
- October 25th, 2012

US-CERT Warns About DKIM Keys After Expert Finds Google Emails Easy to Spoof
Companies such as Yahoo!, Amazon, PayPal, eBay and HSBC are also affected
- Security Fixes and Improvements
- By Eduard Kovacs
- October 24th, 2012

Flaws in Airline Boarding Passes Could Allow Terrorists to Carry Illegal Items on Board
The barcode reveals if the passenger will undergo conventional screening or not
- Security Blog
- By Eduard Kovacs
- October 23rd, 2012
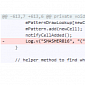
Android ROM Installed on 2.5 Million Devices Found to Log Unlock Patterns
Developers have addressed the issue that plagued Cyanogen Mod