- Security Fixes and Improvements
- By Eduard Kovacs
- November 26th, 2012

Expert Finds 23 Security Holes in Schneider, Rockwell, Other SCADA Systems
Researchers claim that many SCADA vulnerabilities are easy to find
- Security Blog
- By Eduard Kovacs
- November 26th, 2012
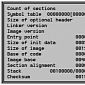
Database-Destroying Narilam Malware Almost Extinct, Experts Say
Researchers haven't been able to find any links to Stuxnet, Duqu, Flame or Gauss
- Security Blog
- By Eduard Kovacs
- November 23rd, 2012
Numerous .eu Domains Registered to Host BlackHole Exploit Kit
The cybercriminals are using a server located in the Czech Republic
- Virus alerts
- By Eduard Kovacs
- November 23rd, 2012
Narilam Worm Targets Corporate Databases from the Middle East
The malware is designed to modify and remove certain items
- Security Blog
- By Eduard Kovacs
- November 22nd, 2012

Experts Find Way to Crack Default WPA2 Passwords of Belkin Routers
The company hasn't collaborated with the researchers in addressing the issue
- Security Blog
- By Eduard Kovacs
- November 21st, 2012
Password-Stealing Malware Passteal Distributed via File Sharing Sites
A new variant has been found to rely on WebBrowserPassView to access sensitive data
- Virus alerts
- By Eduard Kovacs
- November 21st, 2012
Operation High Roller: Cybercriminals Target European SEPA Network
McAfee researchers have analyzed the latest attacks targeting German banks
- Security
- By Eduard Kovacs
- November 20th, 2012

Security Predictions for 2013 Provided from Three Different Angles
Experts from GlobalSign, Solutionary and SpectorSoft share some insight
- Virus alerts
- By Eduard Kovacs
- November 20th, 2012

Linux Rootkit, Perfect for Targeted Attacks and Drive-by Download Scenarios, Found
Experts from Kaspersky and CrowdStrike have analyzed the new threat
- Security
- By Eduard Kovacs
- November 19th, 2012

Even Small and Unimportant Security Bugs Matter in Java, Experts Say
Security Explorations has released an interesting technical report on Java SE security
- Security Blog
- By Eduard Kovacs
- November 14th, 2012

Experts Find Ransomware That Works on Windows 8
Trojan.Ransomlock.U has no problem in locking the screen of computers that run the new OS
- Virus alerts
- By Eduard Kovacs
- November 14th, 2012
Malware Uses Social Media and Blogging Sites as Part of Its C&C Server
FireEye researchers have analyzed an interesting threat
- Security Blog
- By Eduard Kovacs
- November 13th, 2012

Young Indian Hacker Claims to Have Created Windows Phone 8 Malware
The prototype is capable of stealing all sorts of information
- Security Fixes and Improvements
- By Eduard Kovacs
- November 9th, 2012
Facebook Chat Can Be Used to Launch DOS Attacks, Expert Finds
The exploit code has been made available by the researcher
- Security
- By Eduard Kovacs
- November 8th, 2012

QRishing Study: Curiosity Is the Largest Motivating Factor for Scanning QR Codes
Carnegie Mellon University researchers have analyzed a particular type of phishing attacks
- Security Fixes and Improvements
- By Eduard Kovacs
- November 8th, 2012

Cybercrime Investigators Find Adobe Reader X/XI Zero-Day Sold for $50,000 – Video
Currently, the exploit is sold only in closed circles on the black market
- Virus alerts
- By Eduard Kovacs
- November 7th, 2012
Image-Stealing Malware Could Be Upgraded for Sophisticated Attacks
Sophos and McAfee experts continue to examine the threat