In a paper he recently released, Henning Klevjer – an information security student at the University of Oslo in Norway –, shows that cybercriminals may improve phishing attacks by relying on the communications standard known as the uniform resource identifier (URI).
The expert explains that attackers could develop stand-alone phishing pages, the content of which can be encoded in Base64 to mask its real intentions. This encoded page can be then placed inside a URI.
Basically, URIs are URLs that don’t point to remote locations. Instead, they include all the data that’s displayed to the user.
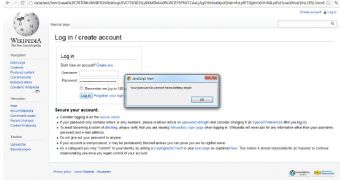
According to Paul Roberts of Sophos, Klevjer demonstrated his findings by creating a fake Wikipedia webpage by utilizing this technique. Apparently, he was able to shrink the fairly large URI (24,682 characters) into only 26 characters by using URL shortening services – which apparently play a key role in these attacks.
“The problem is that there are few defenses against this type of phishing. The web browser will not connect to any external resource to display the phish, unless images are included from remote sites (they could also be embedded). The only limit is whatever size limit to URLs the browser imposes,” Johannes Ullrich of SANS explained.
“From a phishing perspective, this will allow inserting the form, but you will still need a web server to receive the data. Unless of course, you can exfiltrate this via DNS.”
The use of URIs for malicious purposes is not new, but it’s clear that as more research goes into this topic, cybercriminals will turn their attention to it.
Currently, some web browsers are designed to mitigate such attacks. For instance, Chrome blocks redirection to data URLs and newer versions of Internet Explorer limit the amount of data that can be packed into them. However, Opera and Firefox execute them without any difficulties.
 14 DAY TRIAL //
14 DAY TRIAL //