- Virus alerts
- By Eduard Kovacs
- July 18th, 2012

Madi Malware: Another Trojan Targets Organizations from the Middle East
Unlike Stuxnet and Flame, Madi relies on social engineering to infect computers
- Security Fixes and Improvements
- By Eduard Kovacs
- July 17th, 2012

Security Expert “Hacks” Handcuffs Using 3D Printer
A German researcher shows everything there is to know about handcuff security
- Security Fixes and Improvements
- By Eduard Kovacs
- July 17th, 2012

Flaw in Artema Hybrid Terminals Allows Hackers to Collect Payment Card Details
This somewhat controversial discovery might affect a large number of people from Germany
- Apple
- By Eduard Kovacs
- July 17th, 2012
Apple Takes Steps to Mitigate In-App Purchase Flaw
The hacker made some changes to the system to make sure that it’s still operational
- Apple
- By Eduard Kovacs
- July 14th, 2012
Apple’s In-App Purchase System Hacked via Man-in-the-Middle Attack
The method can be used to purchase extensions or extra levels for free
- Security Blog
- By Eduard Kovacs
- July 13th, 2012

Researcher Identifies Critical Vulnerability in Chrome 20 (Video)
Ucha Gobejishvili has published a POC video to demonstrate his findings
- Apple & Mac Blog
- By Eduard Kovacs
- July 13th, 2012
Experts Find Intel OS X Binary in Multi-Platform Malware
The new variant doesn't need additional software to open a reverse shell
- Hacking News
- By Eduard Kovacs
- July 13th, 2012

Yahoo! Hack Could Be More Critical than Firm Claims, Expert Says (Exclusive)
Janne Ahlberg found some noteworthy clues in the Yahoo! data dump
- Spyware Threats
- By Eduard Kovacs
- July 12th, 2012

DarkComet RAT Used to Target Gamers, Military and Governments, Experts Find
Arbor Networks experts analyzed the most interesting of their 4,000 samples
- Virus alerts
- By Eduard Kovacs
- July 12th, 2012
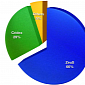
Experts: Phishing Campaigns Changed Since “Blackhole” Came into the Picture
Trend Micro experts published a detailed paper on spam runs that rely on the exploit kit
- Security Blog
- By Eduard Kovacs
- July 12th, 2012

Netflix and YouTube HQ Now a Reality as Nexus Q Gets Hacked
A video has been made to show off the endless possibilities
- Security Blog
- By Eduard Kovacs
- July 11th, 2012

NFC Can Be Used to Steal Files and Take Control of Phones, Expert Says
Charlie Miller will present his findings at Black Hat USA 2012
- Security Blog
- By Eduard Kovacs
- July 10th, 2012

Researchers Identify “Invisible” Data Theft at Black Hat USA 2012
Stochastic forensics can be used to determine if data was copied from a computer
- Virus alerts
- By Eduard Kovacs
- July 10th, 2012

Man-in-the-Mobile Attacks Target the Bank Accounts of Android Users
Individuals from Spain, Portugal, Germany and the Netherlands are potential victims
- Hacking News
- By Eduard Kovacs
- July 9th, 2012

Android “Botnet” Might Involve Yahoo! Mail Session Hijacking, Experts Say
Lookout researchers present a plausible theory regarding the alleged botnet
- Security Blog
- By Eduard Kovacs
- July 6th, 2012

US Authorities Spread Fake Secrets to Identify Leakers
The Pentagon wants to make sure that no more information ends up on Wikileaks
- Security Blog
- By Eduard Kovacs
- July 6th, 2012
Monkif Botnet Avoids Detection by Receiving Commands Encrypted in JPEG Files
McAfee experts have analyzed the threat which seems to use the same server since 2009