- Security Blog
- By Eduard Kovacs
- July 5th, 2012
Flame’s Data Collection Module Detailed by Experts
The advnetcfg.ocx component allowed the malware to stay hidden for such a long time
- Security Blog
- By Eduard Kovacs
- July 4th, 2012
“Printer Bomb” Spreads via .htaccess Redirection Attacks
Over 4,000 websites have been compromised to take part in the scheme
- Security Blog
- By Eduard Kovacs
- July 3rd, 2012
Video: Researchers Develop Rootkit to Highlight Flaws in Android 4.0.4
The malware could replace the legitimate browser with a malicious one
- Virus alerts
- By Eduard Kovacs
- July 3rd, 2012
All Carberp Cybercriminals Arrested, but Infection Rates Still High
ESET and Group-IB researchers have closely investigated the case
- Security Fixes and Improvements
- By Eduard Kovacs
- July 2nd, 2012
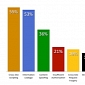
WhiteHat: XSS Most Prevalent Site Vulnerability in 2011
Compared to 2010, the average number of critical flaws per website has dropped
- Interviews
- By Eduard Kovacs
- June 30th, 2012

Softpedia Exclusive Interview: Steven Seeley on the “Ghost” in Windows Allocator
The Stratsec expert presents issues in the heap manager and attack mitigation strategies
- Security Fixes and Improvements
- By Eduard Kovacs
- June 29th, 2012

RiskRanker Detects Mobile Threats Without Relying on Malware Signatures
An innovative solution developed by experts from NQ Mobile and North Carolina University
- Security Fixes and Improvements
- By Eduard Kovacs
- June 27th, 2012

RSA CTO: It’s Not True, SecurID 800 Token Not Cracked
The expert claims that the attack can't be used to gain access to the private key
- Security Fixes and Improvements
- By Eduard Kovacs
- June 26th, 2012

RSA SecurID Cracked, Experts Access Cryptographic Keys in 13 Minutes
Researchers demonstrate that many security tokens are highly vulnerable
- Security Blog
- By Eduard Kovacs
- June 25th, 2012

Android Network Tool-Kit Pentester’s World Cup Launched by Zimperium
The winner will attend this year's Black Hat conference in Las Vegas
- Interviews
- By Eduard Kovacs
- June 23rd, 2012

Softpedia Exclusive Interview: Georgia Weidman on the Android Permission Model
We had the opportunity to talk to the expert at Hack in the Box 2012 Amsterdam
- Security Fixes and Improvements
- By Eduard Kovacs
- June 22nd, 2012

PayPal Launches Paid Bug Bounty Program
Security researchers can submit XSS, CSRF, SQL Injection and authentication bypass flaws
- Security Blog
- By Eduard Kovacs
- June 21st, 2012
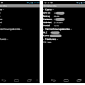
Expert Publishes Android App That Steals Contactless Card Details
The application shows how easy it is to swipe payment card details by using a phone
- Virus alerts
- By Eduard Kovacs
- June 21st, 2012
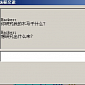
Experts Confronted by Malware Developer While Researching Diablo III Keylogger
The cybercriminal remotely shut down their computer after trying to access their webcam
- Security Fixes and Improvements
- By Eduard Kovacs
- June 21st, 2012

Prepare Your Vulnerabilities, Exodus Has Launched Its Intelligence Program
Submit your findings and in 10 business days you'll learn if it's of value
- Security
- By Eduard Kovacs
- June 20th, 2012

Bruce Schneier on Flame-Like Malware: It’s All About the Way It Spreads
The expert believes that all developers test their malware against antivirus software
- Advisories
- By Eduard Kovacs
- June 20th, 2012

Researcher Explains Why Scammers Say They Are from Nigeria
A great study that shows the challenges faced by fraudsters