Security researchers have identified a registry in both Windows 7 and Windows 8 which contains user password hints. The precious data is encoded, but as experts have demonstrated, it’s not that difficult to break the encryption.
Passwords are a hot topic these days. If users choose them wisely and keep them secure, companies are the ones to expose them. In other cases, when website owners make sure that their systems are bulletproof, their customers choose passwords such as “123456.”
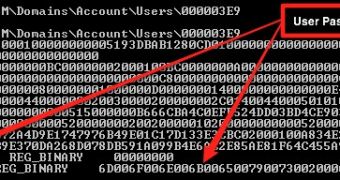
This is another article about password security and it’s based on research performed by Trustwave’s SpiderLabs. They identified a registry key called “UserPasswordHint” in the SAM database, located at HKLM\SAM\SAM\Domains \Account\Users \<userkey>\UserPasswordHint.
A system administrator can easily read the key by doing a query, but as expected, the hint is encrypted. However, this turned out not to pose such a great challenge to the experts after they noticed a pattern of zeroes (see screenshot).
“Having dealt with a fair amount of PHP malware in the last couple months, one of things the 'baddies' do is chunk up their payload data into individual characters and then encode them in their ASCII numerical representation,” Jonathan Claudius of SpiderLabs explained.
“Well in looking at this registry value, it seemed to follow a similar approach, so I wrote a little decoder in Ruby to see if I could learn this users password hint.”
The decoder worked perfectly and in no time the password hints were revealing themselves.
Since this could be of great aid to penetration testers, the experts integrated the decoder into Metasploit.
While the exposure of password hints could represent a risk for users, in reality, it shouldn’t. Microsoft, for instance, recommends customers to choose a hint that is “vague enough so that nobody else can guess the password, but clear enough that it will remind them of their password.”
 14 DAY TRIAL //
14 DAY TRIAL //