- Virus alerts
- By Eduard Kovacs
- July 16th, 2013
Fake Chinese Ministry of Defense Emails Used in Attacks on Asian and European Governments
16 European officials have received the malicious messages
- Security Fixes and Improvements
- By Eduard Kovacs
- July 1st, 2013

Experts Warn of Unpatched Backdoor in Atlassian Crowd Authentication Service
The vulnerability can be exploited to compromise credentials
- Security Blog
- By Eduard Kovacs
- June 26th, 2013

Expert Identifies Backdoor in HP’s StoreOnce Backup System (Updated)
The researcher is unhappy that HP hasn't addressed the issue
- Security Blog
- By Eduard Kovacs
- June 15th, 2013
Trojan Uses Fake Adobe Certificate to Evade Detection
Symantec experts have analyzed an interesting variant of Backdoor.Trojan
- Security Blog
- By Eduard Kovacs
- June 6th, 2013
German Users Targeted with Malware Capable of Wiping MBR
Trend Micro has analyzed an interesting backdoor malware
- Security Blog
- By Eduard Kovacs
- May 10th, 2013
Winnti Backdoor Created with Aheadlib to Mimic Legitimate System Library
Trend Micro experts have analyzed this interesting threat
- Virus alerts
- By Eduard Kovacs
- April 30th, 2013

Sophisticated Apache Backdoor Used to Drive Traffic to Malicious Websites
Sucuri and ESET experts have analyzed this threat
- Security Blog
- By Eduard Kovacs
- April 24th, 2013
Vernot Trojan Avoids Detection by Using Blogging Platform for C&C Communications
Drafts saved on a Japanese service are used for backdoor commands and other tasks
- Security Blog
- By Eduard Kovacs
- April 20th, 2013

Former Hostgator Employee Accused of Installing Backdoors on Over 2,700 Servers
The malicious apps were discovered after the suspect was terminated
- Apple & Mac Blog
- By Filip Truta
- March 12th, 2013

New Trojan Bypasses OS X Gatekeeper
The same piece of malware was recently used to hack Apple, Twitter, and Microsoft
- Security Blog
- By Eduard Kovacs
- March 5th, 2013
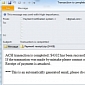
ACH Scam Alert: Transaction Is Completed
The malicious emails are designed to distribute Backdoor.Agent
- Security Blog
- By Eduard Kovacs
- February 12th, 2013

Frutas: Java-Based Cross-Platform RAT
Symantec experts have analyzed the tool that is mainly used by Spanish hackers
- Security Blog
- By Eduard Kovacs
- February 4th, 2013
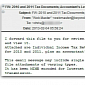
Malware Alert: 2010 and 2011 Tax Documents, Accountant's Letter
Sophos experts have examined this latest spam run
- Virus alerts
- By Eduard Kovacs
- February 1st, 2013
At Least 12 Organizations from Aerospace and Defense Industry Targeted by Hackers
The malware used in this campaign is identified by Symantec as Backdoor.Barikiofork
- Security Blog
- By Eduard Kovacs
- January 18th, 2013
Hackers Hide Backdoor Malware in Fake “Java Update 11”
Trend Micro experts have analyzed the malicious element
- Security Blog
- By Eduard Kovacs
- December 10th, 2012
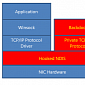
Exforel Backdoor Implemented at NDIS Level to Be More Stealthy
Microsoft Malware Protection Center researchers have analyzed the threat
- Security Blog
- By Eduard Kovacs
- November 20th, 2012

Hackers Target NATO with Hurricane Sandy Emails
A malicious document was sent to NATO Special Operations Headquarters in October