Security firm Symantec has uncovered a cybercriminal campaign that has targeted at least 12 different organizations from the defense and the aerospace industry, including defense contractors, government agencies, and aviation and traffic control companies.
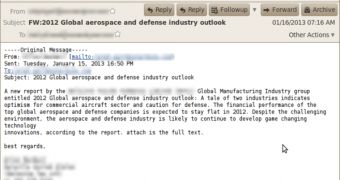
The attacks start with a spear phishing email entitled “FW: 2012 Global aerospace and defense industry outlook.”
The emails have been sent to individuals who hold important roles in the targeted organizations, such as directors and vice presidents. To make them more legitimate-looking, the messages always appear to come from the targeted company’s employees or from individuals within the industry.
The PDF file that’s attached to the email appears to represents a copy of the “Global aerospace and defense industry outlook” report.
However, when it’s executed, it not only opens a genuine document, but it also attempts to exploit a remote memory corruption vulnerability that plagues older versions of Adobe Flash Player.
“In addition to the clean PDF file, the threat drops a malicious version of the svchost.exe file. This file then drops a malicious version of ntshrui.dll into the Windows directory,” Symantec’s Satnam Narang explained.
“The threat leverages a technique known as DLL search order hijacking (the ntshrui.dll file is not protected by KnownDLLs). When the svchost.exe file calls the explorer.exe file, it will load the malicious ntshrui.dll file in the Windows folder instead of the legitimate ntshrui.dll file in the Windows system directory.”
The malware, identified by Symantec as Backdoor.Barikiofork, is capable of enumerating disk drives, contacting the command and control server, collecting system information, and downloading and executing additional updates.
Symantec advises organizations to deploy proper email security mechanisms to prevent such attacks. It’s also worth noting that the vulnerability leveraged in this case by the malware has been patched a long time ago, so companies that keep their software updated at all times have a better chance at mitigating the attacks.
 14 DAY TRIAL //
14 DAY TRIAL //