- Security Blog
- By Eduard Kovacs
- November 7th, 2012

Gh0st RAT and ADDNEW Backdoor Found Working Side by Side
FireEye researchers say the two are a "match made in heaven"
- Spam Reports
- By Eduard Kovacs
- October 12th, 2012
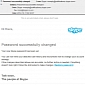
“People at Skype” Return, Send Out Malicious Password Notifications
Cybercriminals are leveraging the news about the new worm to induce panic
- Security Blog
- By Eduard Kovacs
- September 26th, 2012

SourceForge: 400 Users Have Downloaded Corrupted phpMyAdmin
The malicious distribution was served from a Korean mirror
- Security Blog
- By Eduard Kovacs
- September 25th, 2012

Backdoor in phpMyAdmin Allows Hackers to Execute PHP Code
Only a particular distribution from SourceForge.net is affected
- Security Blog
- By Eduard Kovacs
- September 25th, 2012
Imuler.B Mac Malware Designed to Avoid Wireshark, Experts Say
The new version of the Mac OS X threat comes with some improvements
- Virus alerts
- By Eduard Kovacs
- August 23rd, 2012
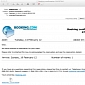
Androm Trojan Variant Comes in Fake Booking.com Emails
The company is warning customers to be on the lookout for such notifications
- Apple & Mac Blog
- By Eduard Kovacs
- July 13th, 2012
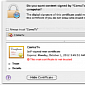
Experts Find Intel OS X Binary in Multi-Platform Malware
The new variant doesn't need additional software to open a reverse shell
- Security Blog
- By Eduard Kovacs
- July 11th, 2012
Backdoor Served on Colombian Site Affects Mac, Windows and Linux Users
A malicious .jar file serves a piece of malware after determining the platform
- Security Blog
- By Eduard Kovacs
- June 29th, 2012
APT Attacks Rely on New Mac OS X Backdoor to Target Uyghur Activists
Backdoor.OSX.MaControl.b steals files and executes commands on the infected machine
- Spyware Threats
- By Eduard Kovacs
- June 5th, 2012

Microsemi Denies Putting Backdoors in Chips
A plot against the US or a clever scenario meant to make China even more "evil"
- Virus alerts
- By Eduard Kovacs
- June 4th, 2012
Malicious PowerPoint Presentations Exploit Flash Vulnerability to Drop Backdoor
Event innocent-looking files can hide a piece of malware
- Spyware Threats
- By Eduard Kovacs
- May 30th, 2012

Backdoor Uncovered in Chinese Chips Used by US Military, Findings Questioned
Cambridge University experts made available the results of their research
- Spam Reports
- By Eduard Kovacs
- March 1st, 2012

Jeremy Lin Malware Exploits Vulnerabilities in Microsoft Office
Cybercriminals rely on the NBA star's life story to spread their malware
- Virus alerts
- By Eduard Kovacs
- January 7th, 2012

DotA 2 and Diablo III Beta Testing Cracks Come with Backdoor Trojans
Beware of phony beta and demo versions found on file-sharing sites
- Security Blog
- By Eduard Kovacs
- December 13th, 2011
Antivirii 2011 Scares Users With Fake Infections
Another piece of scareware has been spotted by security experts
- Spam Reports
- By Eduard Kovacs
- December 13th, 2011
Nitro Cybercriminals Continue Targeting Chemical Companies
The hackers have slightly changed their spam emails, but the MO is still the same
- Virus alerts
- By Eduard Kovacs
- November 24th, 2011

Hackers Use Vulnerabilities in Korean Office Software
Another fine example of why applications should always be kept up to date