Even though at the end of October the security firm Symantec published a paper on the so-called Nitro attacks that target secrets from the chemical industry, a report issued yesterday states that the same hackers are still active.
The methods utilized by the crooks to infiltrate chemical companies are basically unchanged. They still rely on the same social engineering techniques, sending out emails that pretend to come from the organization’s internal IT staff, informing recipients on a security update.
Furthermore, the latest variant of the archive attached to the emails, the one that hides the infamous Poison IVY Backdoor, comes with a copy of Symantec’s report, in the attempt of making the whole thing seem more legit.
“Dear customer, Recently poison Ivy Trojan horse rampant, many enterprises are infected. Symantec has launched a special kill poison Ivy Trojan anti-virus software,” reads the message signed Symantec Technical Support Department.
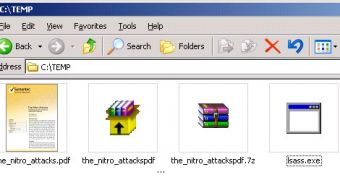
The attachment is a 7Zip archive that contains an element called “the_nitro_attackspdf .exe”, the large number of spaces between “attackspds” and “exe” being carefully placed to fool the users into believing that the file is actually a document instead of an executable.
When launched, Poison IVY, which masquerades itself in a file called Isass.exe, steps into play and tries to connect to luckysun.no-ip.org, a domain hosted by the same provider as before.
“Despite the publishing of the whitepaper, this group persists in continuing their activities unchecked. They are using the exact same techniques - even using the same hosting provider for their command and control (C&C) servers,” researchers Tony Millington and Gavin O’Gorman said.
The domains used in the attack were disabled and the security solutions company contacted the hosting provider to make sure the necessary steps are taken. The emails sent in the malicious campaign are being closely monitored and blocked by their .cloud email scanning service.
 14 DAY TRIAL //
14 DAY TRIAL //