- Security Blog
- By Ionut Ilascu
- August 14th, 2014

Shanghai Officials Change iPhone, Samsung Phones for Alternative with Encryption Functionality
Move made in the wake of recent news on iPhone being surveillance prone
- Security
- By Ionut Ilascu
- August 12th, 2014
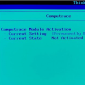
Millions of Computers Have Backdoor Enabled by Default
Legitimate software behaves like malware, whitelisted by antivirus products
- Security
- By Ionut Ilascu
- August 6th, 2014

The FBI Relies on Malware to Catch Criminals
The bureau uses backdoors or special code to collect details identifying the machine
- General Business
- By Bogdan Popa
- July 28th, 2014

Microsoft Says the US Never Asked to Put a Backdoor in Its Software
Company official says backdoors could destroy the whole business
- Security
- By Ionut Ilascu
- July 26th, 2014

New Trojan Infiltrates Korean Organization
Identifying the threat actor proves to be quite difficult
- Security
- By Ionut Ilascu
- July 24th, 2014

Apple Downplays Severity of “Backdoors” in iOS
Company creates knowledge base page for hidden services in iOS
- iWorld
- By Adrian Boioglu
- July 23rd, 2014

Apple Denies Backdoor Data Allegations, Calls Them "Diagnostic Capabilities"
Apple was accused of letting government agencies have access to iOS
- Security Fixes and Improvements
- By Ionut Ilascu
- July 15th, 2014
Backdoor Uploading Allowed by WPtouch Plugin for WordPress
The component is very popular, has more than 5 million downloads
- Security
- By Ionut Ilascu
- July 4th, 2014

Kivars Malware Adapted for 64-bit Systems
Slightly different from the 32-bit version, preserves functionality
- Security
- By Ionut Ilascu
- July 2nd, 2014
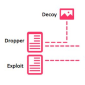
CosmicDuke Malware Combines Components from Cosmu and MiniDuke
Steals passwords and files, takes screenshots, logs keystrokes
- Security
- By Ionut Ilascu
- June 20th, 2014
Government Employees Targeted by Phishing Campaign
Malware has evasion capabilities for specific security solution
- Online Surveillance
- By Gabriela Vatu
- June 20th, 2014

US House Finally Takes Measures Against NSA Mass Surveillance
The move cuts down funds for NSA's backdoors in hardware and imposes the need for warrant, but it may not be enough
- Security Blog
- By Ionut Ilascu
- June 13th, 2014
Web Diary Professional Exploited by Cybercrooks
Despite being obsolete, many admins cling to the vulnerable solution
- Security
- By Eduard Kovacs
- March 19th, 2014

Edward Snowden: Backdoors Planted by the NSA Can Also Be Leveraged by Others
The whistleblower has attended TED via a telepresence robot
- Security
- By Eduard Kovacs
- March 18th, 2014
Fake Video About Malaysian Airlines Flight MH370 Hides Malware
The number of scams leveraging the story of the missing plane is growing
- Security Blog
- By Eduard Kovacs
- March 14th, 2014
Cybercriminals Leverage Mass Stabbing in China to Distribute Gh0st RAT
A backdoor is hidden inside a harmless-looking document file
- Security Blog
- By Eduard Kovacs
- March 14th, 2014
Invitations for Grand Theft Auto 5 PC Beta Testing Hide Malware
Don’t trust websites or emails promising GTA 5 for PC