One of the best ways for pieces of malware to avoid being detected by security solutions is to rely on legitimate applications and services to perform their malicious tasks. One perfect example is the Vernot Trojan.
Trend Micro has analyzed a new variant, BKDR_VERNOT.B, which relies on a Japanese blogging platform for command and control communications.
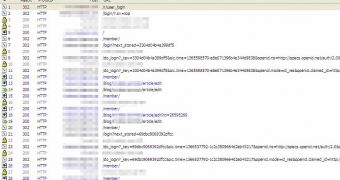
Once it infects a machine, Vernot logs into an account on the Japanese blogging site and creates a draft which it names after the victimized machine.
This draft is later used for various purposes, including to drop off stolen information and receive backdoor commands. These commands include downloading files, executing files, renaming files, and extracting files from archives.
Each time one of the commands is executed, a string is added to the blog draft.
This technique ensures that security solutions don’t easily detect the threat because communications between the computer and a legitimate blogging platform don't appear malicious.
Previous variants of Vernot abused Evernote to hide their presence.
 14 DAY TRIAL //
14 DAY TRIAL //