- Weekly Roundup
- By Ionut Ilascu
- November 12th, 2014

Air-Gapped Systems Targeted by Sednit Espionage Group
The group is believed to operate since 2005
- Spyware Threats
- By Ionut Ilascu
- November 11th, 2014
Darkhotel Espionage Group Targets Executives Staying at Luxury Locations
The group relies on highly advanced zero-day exploits
- Security
- By Ionut Ilascu
- November 4th, 2014
BlackEnergy APT Targets a Diverse Crowd of Victims
Some of the victims are from Europe, Middle East and Asia, but the United States has also been affected
- Security
- By Ionut Ilascu
- November 3rd, 2014

BlackEnergy APT Has a Rich List of Plug-ins for Windows and Linux
Malware structure hints at highly organized team behind it
- Security
- By Ionut Ilascu
- October 28th, 2014
Chinese APT Group Axiom Is Highly Technical and Disciplined
Group exhibits rarely seen level of sophistication
- Security
- By Ionut Ilascu
- October 28th, 2014
Sophisticated Chinese Espionage Group After Western Advanced Technology
Axiom APT group serves China's strategic interests
- Security
- By Ionut Ilascu
- October 28th, 2014

Keylogging Framework Used by Multiple Actors in Watering-Hole Attacks
ScanBox targets a diverse set of organizations
- Security
- By Ionut Ilascu
- October 23rd, 2014
Sednit Malware Used in Operation Pawn Storm Espionage Campaign
Very specific victims targeted through spear phishing
- Security Blog
- By Ionut Ilascu
- October 22nd, 2014

Google Drive Used to Host Reconnaissance Data from Government Computers
Uploading docs to the cloud is all the malware piece can do
- Security
- By Ionut Ilascu
- October 22nd, 2014

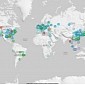
Cyber-Attacks Represented in Threat Map
Visual representation is based on real information
- Advisories
- By Ionut Ilascu
- October 22nd, 2014

New Windows Zero-Day Flaw Leveraged in the Wild
Vulnerability affects all Windows versions save Server 2003
- Editorials
- By Ionut Ilascu
- October 19th, 2014

There's a Silver Lining in the Fight Against Cyber Espionage
Shared threat intelligence helps connect attacks from the same threat actor and indetify the different tools they use
- Security
- By Ionut Ilascu
- October 15th, 2014

Cyber Espionage Group Leverages at Least Ten Custom Tools in Attacks
Group relies even on rootkit code intended for research
- Security
- By Ionut Ilascu
- October 15th, 2014

Security Firms Form Coalition to Crack Down on Cyber Espionage Group
Hacker groups spied on organizations for at least four years
- Security
- By Ionut Ilascu
- October 14th, 2014

Cyber Espionage Group Exploits New Windows Zero-Day to Get Elevated Privileges
Group is believed to operate under the Chinese flag
- Security
- By Ionut Ilascu
- October 14th, 2014
Five-Year Long Russian Cyber Espionage Campaign Exploits Windows Zero-Day
Vulnerability affects all Windows desktop editions save XP
- Security
- By Ionut Ilascu
- October 10th, 2014

China Makes Efforts for Better Cyber Security Reuters
Attack seems to be China's defense strategy