- Editorials
- By Ionut Ilascu
- April 5th, 2015

Volatile Cedar Cyber Spying Op May Not Be the Work of a Foreign Country
Campaign focused on intelligence gathering since 2012
- Security
- By Ionut Ilascu
- April 1st, 2015

Most Victims Targeted by Volatile Cedar Group Are from Lebanon
Infections also seen in US, UK, Canada, Israel and Russia
- Security
- By Ionut Ilascu
- March 31st, 2015
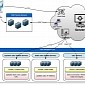
“Explosive” Malware Used by Cyber-Espionage Group Working from Lebanon
Volatile Cedar operation tied to Lebanese political group
- Security
- By Ionut Ilascu
- February 19th, 2015

French Intelligence Spy Tool “Babar” Analyzed
No malware attribution from security researchers
- Security
- By Ionut Ilascu
- February 19th, 2015

DoubleFantasy Is Equation Group’s First Attack Wave
Infection starts with running multiple exploits in a loop
- Security
- By Ionut Ilascu
- February 18th, 2015
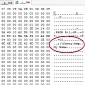
Fanny Worm Has Been Freely Available for Download for Almost Five Years
Poster received no advice for malware removal until today
- Security
- By Ionut Ilascu
- February 10th, 2015

Anthem Network May Have Been Compromised Since April 2014
Hackers create alternate network to prepare the attack
- Security
- By Ionut Ilascu
- February 4th, 2015

iOS Devices Targeted by Cyber-Espionage Campaign
Two spyware samples have been linked to Sednit malware
- Security
- By Ionut Ilascu
- January 19th, 2015

China Stole F-35 Fighter Jet Plans, Snowden Leak Confirms
North Korea spied on through “fourth party” data collection
- Incidents
- By Ionut Ilascu
- December 30th, 2014
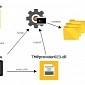
Havex RAT Authors Self-Sign Malware to Appear from IBM, 64-Bit Version Spotted
Threat actors are expected to continue to modify the threat
- Security Blog
- By Ionut Ilascu
- December 29th, 2014

Angela Merkel’s Staff Member Targeted with Regin Advanced Persistent Threat
Malware infects USB of senior aide, is stopped by antivirus
- Security
- By Ionut Ilascu
- December 15th, 2014

FBI “Flash” Report Warns US Businesses of Iran-Based Hacking Activities Reuters
Attacks initiated from IP addresses from Iran
- Virus alerts
- By Ionut Ilascu
- December 13th, 2014
Solaris Boxes Possibly Targeted by Linux Turla Backdoor, Too
Researchers expect to see Solaris machines infected by Turla
- Security
- By Ionut Ilascu
- December 11th, 2014

Kaspersky Launches Map of Advanced Persistent Threats
Collection of rare, advanced malware with useful information
- Security
- By Ionut Ilascu
- December 11th, 2014

Predictions for APT Attacks Go from Bad to Worse in 2015
Complexity of cyber-espionage campaigns will increase, more threat actors will join the cyber war scene
- Security
- By Ionut Ilascu
- December 10th, 2014

Red October Cyber Spy Op Goes Mobile via Spear-Phishing
Malware ready for Android, iOS and BlackBerry, over 60 mobile operators included in the preparations
- Virus alerts
- By Ionut Ilascu
- December 10th, 2014
Red October Cyber Espionage Campaing Resurrected with “Cloud Atlas” Malware
Threat actor targets the same victim profile, most victims have been detected in Russia and Kazakhstan