An active threat actor has been relying on compromising hotel networks to reach high value targets from different industries since at least 2010, but some of the tools it used date as far back as 2007.
Dubbed Darkhotel, the espionage group is well resourced, and in order to complete the mission, it is not reluctant to use zero-day exploits (for Internet Explorer and Adobe products) even if these are at risk of being discovered, researchers at Kaspersky found.
Spear-phishing used for targeting the victims
Victims observed by the security experts include CEOs, vice presidents, sales and marketing directors, and top staff in research and development at companies doing business or outsourcing in the Asia-Pacific (APAC) region.
They are connected to industries such as electronics manufacturing, pharmaceuticals, investment capital and private equity, automotive, defense industrial base, as well as different NGOs.
The Darkhotel actor, also known as Tapaoux, is selective in choosing the victims and operates by delivering malware guised as updates for major software through malicious iframes injected in the log-in web portals of hotels accommodating the target.
“This group of attackers seems to know in advance when these individuals will arrive and depart from their high-end hotels. So, the attackers lay in wait until these travelers arrive and connect to the Internet,” Kaspersky says in a report released on Monday.
After the victim checks out of the hotel, all traces of the tools employed in the incident are removed, the threat actor thus maintaining a hidden status.
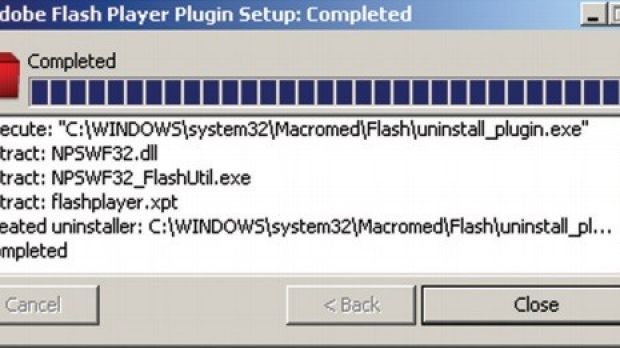
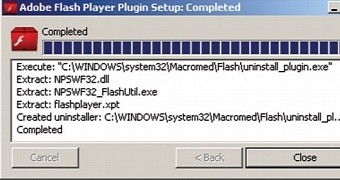
The Darkhotel actor uses digital certificates to sign its attack tools, Kaspersky believing that the group duplicated the keys (MD5 RSA 512-bit) after cracking them, since the cost associated with this process is low.
Infrastructure is riddled with weaknesses, contrary to attack method used
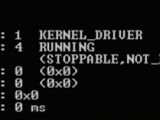
It has been observed that the most used tool was an advanced, digitally signed keylogger that functions at kernel level.
Additional crimeware associated with the group includes downloaders, infostealers, Trojans and malware droppers. They are detected as Tapaoux, Pioneer, Karba and Nemim.
Contrary to the skillset demonstrated by the attack vectors and the tools used, the malicious actors seem to rely on an infrastructure with “weak server configurations with limited monitoring and defensive reactions, and making some simple mistakes,” the researchers write in the report.
As far as the origin of the victims is concerned, the security experts determined that most of them are from Japan, Taiwan, China, Russia, Korea and Hong Kong; however, there have been noted targets in Russia, the United States, Germany, Ireland and India.
 14 DAY TRIAL //
14 DAY TRIAL //