A browser-based keystroke interception tool called ScanBox has been observed to be wielded by several threat actors targeting a diverse set of organizations in the US, China, Korea and Japan.
Unlike other tools used in watering-hole attacks, which are built to deliver exploits that would lead to compromising computers of visitors of a specific website, ScanBox contains a keylogging component that does not require running malware from disk. The keystroke interception is done through JavaScript code executed in the context of the browser.
Websites in different activity sectors have been compromised
Since it was first brought to the attention of security experts in August by researchers at AlienVault, the framework has been closely monitored by experts from PricewaterhouseCoopers (PwC), who have found that several actors may be using it for compromising computers.
Since August, the malicious toolset has been observed to aim at four websites: one relating to the industrial sector in Japan, one linked to the Uyghur community in China, a think tank in the US, and a hospitality service in Korea.
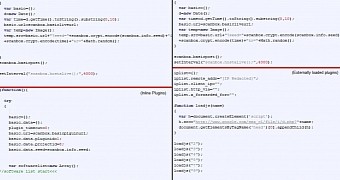
The diverse set of targets was the first clue that more than one operator was behind ScanBox. Closer examination of the code confirmed the suspicions of Chris Doman and Tom Lancaster from PwC, as they found variations in the implementation of the framework.
In some cases, the toolset would selectively load additional plug-ins from separate files, while in others, the malicious code was delivered in a single block of JavaScript.
The two researchers say that the reason for the extra plug-ins is not to raise the alarm through crashes and errors to the owner of the compromised site when the page loads, since they are compatible with specific web browsers.
Threat actors may be sharing the resources for different attacks
Depending on the browser used, ScanBox would deploy reconnaissance software, code for detecting Flash, SharePoint, Adobe PDF Reader and Java. Some of them, including the JavaScript keylogger, are launched on any of the major browsers on the market (Internet Explorer, Mozilla Firefox, Google Chrome and Safari).
In many versions of ScanBox, the researchers found that code publicly available for free was used by the attackers.
Doman and Lancaster admit that there is the possibility that the same actor could be behind the attacks on all four websites, but the fact that “very few attackers have the patience to maintain completely distinct infrastructure with multiple registrars, name servers and hosting providers at the same time” makes them believe that more than one operator works with ScanBox.
Apart from this, the growing trend is sharing of resources between threat actors with the same goal, saving the trouble of creating an additional exploit kit.
 14 DAY TRIAL //
14 DAY TRIAL //