- Security
- By Eduard Kovacs
- April 19th, 2012

5,000 Malicious Android Apps Identified in Q1, 2012
Trend Micro released a report to show the most important threats of 2012
- Security Blog
- By Eduard Kovacs
- April 18th, 2012

Top 10 US Cities for Online Fraud Origination in Q1 2012
New York is ranked number 1 in e-commerce fraud risk
- Security
- By Eduard Kovacs
- April 18th, 2012

Most UK Organizations Unable to Identify Data Breach Victims in 24 Hours
Penalties would motivate many firms to focus their efforts on data breach policies
- Security
- By Eduard Kovacs
- April 5th, 2012

Cybercriminals Dupe Users with Popular Brand Names, Experts Say
GFI's VIPRE report shows the most significant events that occurred in March 2012
- Xbox
- By Andrei Dobra
- April 3rd, 2012

Xbox 720 Out in Late 2013, Requires Always-On Internet, Report Says
More rumors about the next Xbox have surfaced on the web
- Games Blog
- By Andrei Dobra
- March 26th, 2012

Prey 2 Reportedly Canceled, Official Announcement Coming Soon
Bethesda has axed the project coming from developer Human Head
- Security
- By Eduard Kovacs
- March 22nd, 2012

Hacktivists Beat Cybercriminals in Data Thefts in 2011, Verizon Says
Hacktivists steal entire databases, profit-driven hackers only take what they can use
- Security
- By Eduard Kovacs
- March 21st, 2012

Data Breaches: Detection Costs Declined, Notification Costs Increased
Companies have learned to put a greater price on the handling of data breaches
- Security Blog
- By Eduard Kovacs
- March 21st, 2012

Japan and US: Source of Most Cyberattacks Against China
404 Chinese government sites were attacked in 2011
- Security
- By Eduard Kovacs
- March 19th, 2012

Up to 5 Million Computers May Be Exposed to RDP Attacks
It's like the Telnet incident from last year multiplied by 200
- Security
- By Eduard Kovacs
- March 19th, 2012
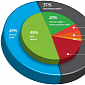
Hackers, Spambots and Other Non-Humans Make 51% of Site Traffic
31% of all the traffic on a website can be malicious
- Security
- By Eduard Kovacs
- March 12th, 2012

Symantec Honey Stick Project: What Happens to a Lost Phone
People who find phones try to access private information even if they return the device
- Security
- By Eduard Kovacs
- March 9th, 2012

Finland Has the Least Malware, Albania the Most
A study performed by Norman reveals global malware infection rates
- Security
- By Eduard Kovacs
- March 6th, 2012
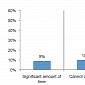
Experts: Data Breaches a Result of Employee Behavior
58% of SMB employees have already clicked on links received via spam emails
- Security
- By Eduard Kovacs
- March 1st, 2012

NASA: Hackers Targeted Us 5,408 Times in 2010 and 2011
A report shows that security incidents even reveals the control algorithm for the ISS
- Security
- By Eduard Kovacs
- February 29th, 2012
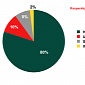
The Longest DDOS Attack in H2 of 2011 Lasted 80 Days
Kaspersky analyzed the DDOS attacks launched in the second part of 2011
- Security
- By Eduard Kovacs
- February 26th, 2012

US Companies Attacked by Competitors, UK Firms by Hacktivists
DDOS attacks against the retail sector may be launched with extortion in mind