- Advisories
- By Eduard Kovacs
- June 20th, 2012

Researcher Explains Why Scammers Say They Are from Nigeria
A great study that shows the challenges faced by fraudsters
- Security
- By Eduard Kovacs
- June 19th, 2012

Money Should Be Spent on Internet Policing, Not Antiviruses, Researchers Say
International scientists found a new way to calculate the costs of cybercrime
- Security
- By Eduard Kovacs
- June 15th, 2012

Admin Accounts and App Backdoors Exploited in Most Data Breaches, Survey
Most IT managers are aware of this, but they still fail to monitor access points
- Virus alerts
- By Eduard Kovacs
- June 12th, 2012

ENISA Publishes Report on Threats from Flame
The paper reminds us of the weaknesses in cyber defenses
- Weekly Roundup
- By Eduard Kovacs
- June 3rd, 2012

Security Brief: Flame, WHMCS and Controversy
The main events of the week between May 28 and June 3
- Security
- By Eduard Kovacs
- June 1st, 2012

AlienVault: Firms Fear That Security Breaches Could Cost Lives
When it comes to snooping, China is held responsible by most companies
- Security Blog
- By Eduard Kovacs
- May 15th, 2012

FBI Confirms Bitcoin Report, But Denies Making It Public
11 agencies worldwide received the document and any one of them could have leaked it
- Security
- By Eduard Kovacs
- May 12th, 2012

TechAmerica: Cybersecurity Keeps Federal Execs Awake at Night
Budget cuts represent another problem for the CIOs of government companies
- Xbox
- By Andrei Dobra
- May 5th, 2012

Xbox 720 Already in Production, Report Says
Microsoft is already building its next-generation home console
- Advisories
- By Eduard Kovacs
- May 2nd, 2012

Experts Make Poll to Better Understand Fake Tech Support Calls
Anyone can complete the ISC survey to help the researchers
- Security
- By Eduard Kovacs
- May 1st, 2012
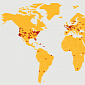
Symantec: 5.5 Billion Attacks Blocked in 2011
The report shows that religious sites were infected with more malware than adult sites
- Security
- By Eduard Kovacs
- April 30th, 2012
AVG: Android Malware Is Pushed via Twitter and Facebook
It's easy to monetize a malicious operation when there are so many potential victims
- Security
- By Eduard Kovacs
- April 28th, 2012
Phishing: Chinese Taobao.com Exceeds PayPal
Chinese cybercriminals rely mostly on newly registered domains instead of hijacked sites
- Virus alerts
- By Eduard Kovacs
- April 26th, 2012
Microsoft: Conficker Still a Threat, Uses Weak Passwords to Spread
The company released its Security Intelligence Report Volume 12
- Advisories
- By Eduard Kovacs
- April 25th, 2012

ICO: Many Fail to Delete Personal Data Before Selling Storage Devices
If not removed, the data can be misused by fraudsters
- Security
- By Eduard Kovacs
- April 25th, 2012
Imperva: Hackers Use Automated Tools in Most Attacks
Havij, SQLmap, and Acunetix are just some of these tools
- Security Blog
- By Eduard Kovacs
- April 23rd, 2012

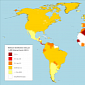
Sophos “Dirty Dozen” Q1 2012 Report: India Is Number 1 Spam Source
The good news is that the number of spam messages worldwide has dropped since 2011