Kaspersky released a report regarding the distributed denial of service (DDOS) attacks that targeted companies in the second half of 2011 and they provided some interesting figures obtained by their botnet monitoring systems.
The numbers reveal that the longest attack recorded in the second half of the past year targeted a travel company and lasted for 80 days, 19 hours, 13 minutes and 5 seconds, and the average duration of DDOS attacks was 9 hours and 29 minutes.
Oddly enough, the largest number of attacks, 384 in number, identified in this period targeted a cybercriminal portal.
The largest attack pushed back by Kaspersky’s DDOS Prevention had a power of 600 megabits per second and the average power was determined to be 100 megabits per second, which translates into a 57% increase compared to the first half of 2011.
Experts believe that the many attacks that were directed against the sites of travel companies, more precisely tour agencies, are a result of corporate sabotage. Most of the hits took place during the holiday seasons which may indicate that some companies wanted to make sure that their competitors are temporarily out of business.
DDOS attacks launched for political reasons also take the podium in the months that passed. Anonymous and other hacktivist collectives relied on such methods to take down government and corporation sites they blamed for doing business in ways that are considered unacceptable by the Internet’s protectors.
Other DDOS related elements that left their mark on the last six months of 2011 include the THC-SSL-DOS tool, which allowed for effective attacks to be launched without using large botnets, and the introduction of the LOIC substitute called RefRef.
Statistically speaking, the attack sources were distributed in 201 countries, the most notable being Russia, Ukraine, Thailand, Malaysia, Mexico and India.
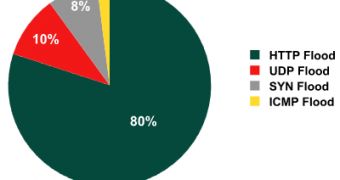
Online shopping, trading, gaming and bank sites were the favorite target of attackers and when it comes to the types of the attacks, HTTP Flood was the most common (80%), followed by UDP Flood (10%) and SYN Flood (8%).
 14 DAY TRIAL //
14 DAY TRIAL //