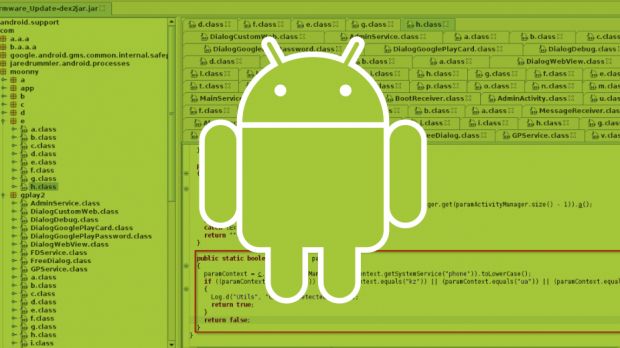
The Android trojan known as Marcher has received an update that now allows it to show fake login screens and steal credentials for various popular Android apps.
Android Marcher appeared on the mobile malware scene in 2013 and initially had the capability of showing a fake screen on top of the Google Play Store app whenever the user started that application.
This screen asked the user to enter their credit card details, which the malware collected and sent to a C&C server.
Later in 2014, the crooks added the ability to phish for banking credentials, mostly from financial institutions in Australia, France, Germany, Turkey, and the US.
Marcher update expands targeting capabilities
An update detected by mobile security firm Zscaler has revealed that, in recent weeks, the trojan has added more items on its target list.
This time around, the trojan's creators focused on popular Android apps instead of banking applications.
Marcher can now collect login credentials by showing a fake login screen whenever the user starts one of these apps: WhatsApp, Viber, Skype, Facebook, Facebook Messenger, Instagram, Twitter, Gmail, Line, UC Browser, Chrome, and the Play store.
As with most malware these days, the stolen data is sent to an online server under the crook's control. While previously this data was transmitted in cleartext via HTTP, recent Marcher versions send it encrypted via an SSL-protected channel.
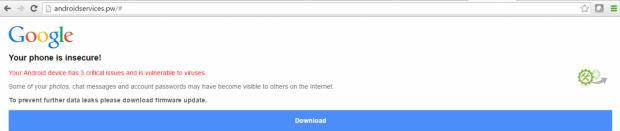
Infections occur via fake Android security updates
This most recent Marcher version reaches Android devices via fake app stores, but Zscaler has also detected crooks using non-official Google domains to spread the malware packed as a fake Android firmware security update.
In the past, the Marcher crew used to pack the trojan as Adobe Flash Player updates (which Android devices don't need or support) and via SMS and email spam.
"These frequent changes clearly indicate active malware development that is constantly evolving - making it the most prevalent threat to the Android devices," says Zscaler's Viral Gandhi.
Users should not install applications from outside the Play Store, even if the Play Store itself has been plagued with malware. The chances of getting infected with malware are much lower via Play Store apps.

 14 DAY TRIAL //
14 DAY TRIAL //