People's obsession with Adobe's Flash Player is putting them and their financial status in harm's way, allowing crooks to trick them into downloading and installing malware-laced Android applications.
Two days ago we wrote on an Android banking trojan which was fooling users into installing a fake Adobe Flash version with the sole purpose of showing phishing pages that stole their banking and Google credentials.
The same technique is also used by another trojan called Android Marcher that relies on a massive SMS and email spam campaign to drive users to adult-themed websites.
There's no Adobe Flash version for Android, so don't fall for this trick
On these sites, in order to view the pornographic videos, users are prompted via a popup to install the Android version of Adobe Flash. Since users won't be able to find it on the official Google Play Store because Adobe discontinued it in 2012, the site offers it to users if they want to download and install it.
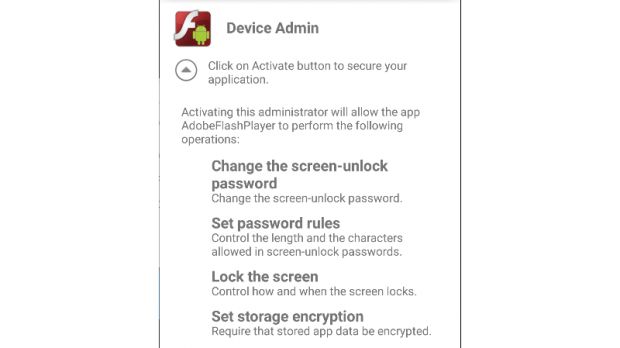
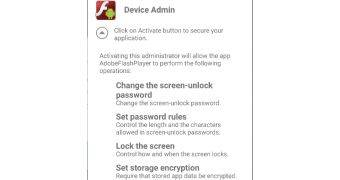
Right from the get-go the app requests admin privileges, and if users are so unaware to know the dangers in allowing an app to run as admin, then the app will have full control over the victim's phone.
Once the infection takes root, the app starts talking to its C&C (command and control) server, sending identification data from the user's device and receiving malicious code that it can use for its attacks later on.
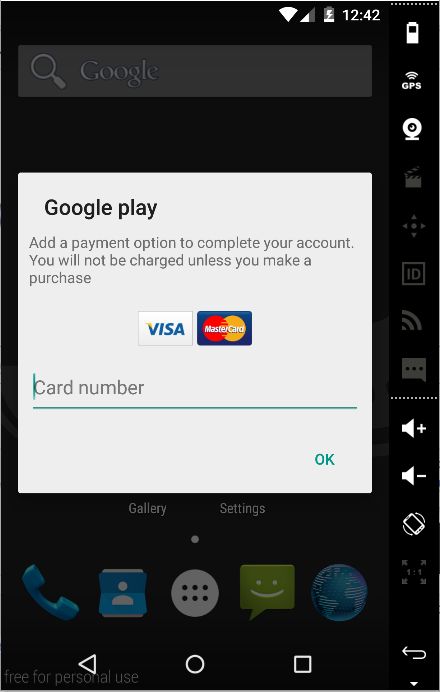
Android Marcher steals credit card data, PayPal and bank logins
This latest campaign uses 50 different versions of Android Marcher, a trojan that was first spotted back in 2013. Like the old versions, these most recent variants come with built-in phishing pages that mimic the Google Play store, asking the user for his credit card information in order to finish the Adobe Flash Player installation.
Users can dismiss this message, but no doubt there will be some people that will trust Google's UI and enter their details.
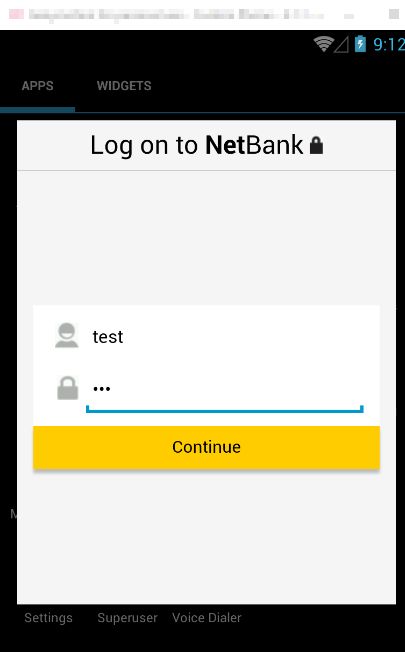
Later on, the trojan will also look for banking apps on the user's device, and if it has support for fake phishing pages, will overlay them over the official app, stealing the user's login credentials for those accounts.
Zscaler says that the following 16 banks are targeted with custom-made phishing pages via Android Marcher: BankSA - Bank of South Australia, Commerzbank, Commonwealth Bank of Australia - NetBank app, Deutsche Postbank, DKB - Deutsche Kreditbank, DZ Bank, Deutsche Bank, Fiducia & GAD IT, ING Direct, La Banque Postale, Mendons, NAB - National Australia Bank, Santander Bank, Westpac, and the WellStar Billpay app. The PayPal Android app is supported as well.
Trojan also tries to trick users into installing the X-VIDEO app
Besides these apps, Zscaler security researchers also noticed that as soon as the Android Marcher fake Adobe Flash Player installation finishes, the app also redirects the user to the real Google Play Store in the hope of making him install the X-VIDEO app.
Researchers reported this app to Google, who rechecked it and found no trace of malicious behavior, but said they'd be keeping an eye on it from now on.
From its description, X-VIDEO is an app for streaming content from one's smartphone to his TV or vice-versa. For now, the app looks safe, but its name being present in a malware campaign may not be its biggest problem since most users are reporting constant crashes.
 14 DAY TRIAL //
14 DAY TRIAL //