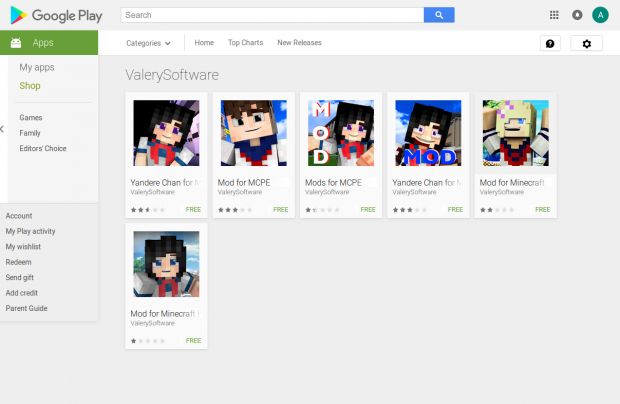
Six apps from a developer named ValerySoftware have found their way into the official Google Play Store and have infected at least 3,000 users, based on their current download counts.
The apps, discovered and reported this week by Intel McAfee security experts, are nothing more but hollow shells providing no functionality at all, except for the malicious features.
Apps specialized in showing ads, downloading & installing other apps
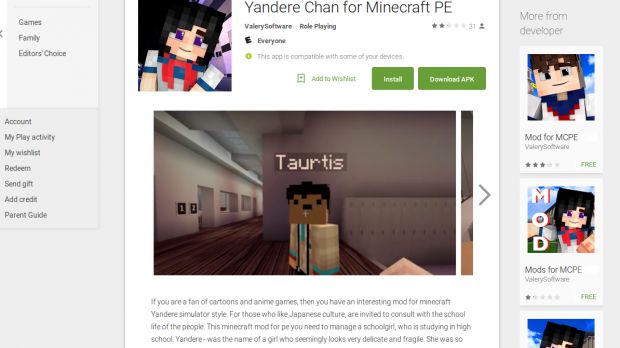
Advertised as all sorts of Minecraft mods, the apps are capable of collecting sensitive information from the phone, downloading Android apps from external sources or the Google Play Store.
The malicious apps can also install the previously downloaded apps, uninstall them, and open or close applications on demand, based on commands received from a central command server.
Additionally, the malicious app will use advertising SDKs to load and show ads from various vendors, silently tapping the ads behind the scenes.
All apps ask users for administrator rights
All of this is possible because the apps require administrator rights at installation time. Since the apps are installed from the Google Play store, users are generally willing to grant them such powers, even if the underlying app is only a silly game mod and doesn't have a reason to require admin privileges.
The reason for requiring admin-level access is to make it much harder to remove the apps after they were installed, something that most users providing feedback on the apps' Google Play pages have complained about.
"I tried for mabye a month and still won't delete," wrote user Denise Travis. "I hate it and it won't work or delete," said Xavier Martinez.
Apps have ties to a well-known cyber-criminal group from Europe
Intel McAfee experts noticed that all apps were encrypted and obfuscated at many levels, which might explain why Google didn't detect their malicious behavior during the automated security tests it performs before approving the apps on the Play Store.
For its part, Intel McAfee has noticed that the app uses domain names previously associated with other cyber-criminal activity, meaning the apps are part of a well-oiled cyber-crime syndicate.
"Based in the domain owner’s information in this malware, we can tie the authors to a group of known cybercriminals in Europe who host and distribute malware," experts wrote.
At the time of writing, all malicious ValerySoftware apps reported by Intel McAfee are still available for download. Intel McAfee detects these threats as Android/Agent.FL.
 14 DAY TRIAL //
14 DAY TRIAL //