Targeted attacks can easily compromise more than half of critical infrastructure systems because of ICS stations that run outdated installations of Windows systems which no longer receive security updates from Microsoft according to CyberX's 2019 Global ICS & IIoT Risk Report.
The report is based on extensive analysis of data collected from real-world traffic from more than 850 industrial control system (ICS) and Supervisory Control and Data Acquisition (SCADA) networks in production over a period of 12 months, from all industrial sectors (e.g., manufacturing, chemicals, utilities, energy, chemicals) across six continents.
Because CyberX's report is based on actual captured data from ICS networks instead of information assembled from surveys, the results are more representative of the current state of SCADA, ICS, and Operational Technology (OT) security.
"If you are in critical infrastructure you should plan to be targeted. And if you’re targeted, you will be compromised. It’s that simple," said Andy Bochman, senior grid strategist for National and Homeland Security at the Idaho National Laboratory (INL) to CyberX.
During 2018 most ICS have remained soft targets for threat actors, with a multitude of attack vectors ranging from plain text passwords and device connected to the Internet to misconfigured wireless access points (WAPs) and weak anti-malware protection.
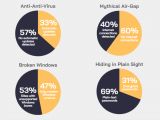
Almost 70% of all investigated ICS networks expose plain text passwords because of SNMP- and FTP-based communication
More precisely, 69% of all industrial sites analyzed by CyberX have passwords send through the network in plain text because of antiquated internet and network protocols such as SNMP and FTP used by ICS stations to communicate with each other.
Another 40% of sites are exposed to the Internet via a direct connection, making them an inevitable target for attackers and increasing the overall attack surface of the critical infrastructure they are part of.
In addition, 57% of ICS networks have anti-malware protection which does not come with a built-in automated signatures updating system, exposing them to newer malware strains and making the AV solution ineffective on the long run.
An extra 16 percent were running at least one Wireless Access Point (WAP) with misconfigured settings which would allow unauthorized remote third parties to access internal ICS network components.
These WAPs can be used as entry points by complex malware such as VPNFilter, a multi-stage modular malicious framework estimated to have indiscriminately infected at least 500,000 Internet-connected devices from 54 countries around the globe at its peak, from routers to QNAP network-attached storage (NAS) devices.
The good news is that ICS stations running legacy Windows systems have dropped from 75% to 53% since 2017
Critical infrastructure networks that were part of CyberX's study also had a remotely accessible device in 84% of cases, with remote access and management services such as RDP, VNC, and SSH running at all times allowing for simple remote management and for easier exploitation by an eventual attacker.
Last but not least, CyberX also found that around 53% of all critical infrastructure sites it analyzed were still using ICS stations that run legacy Windows installations which no longer receive security updates from Microsoft and are acting as open security gaps to APT groups such as BlackEnergy or the recently unveiled GreyEnergy.
CyberX's report also comes with some good news seeing that the stats have significantly improved from roughly 75% of ICS networks having outdated Windows-based systems in 2017 to the 53% found during 2018's analysis.
"We’re not here to create FUD, but we think it’s important for business leaders to have a data-driven view of ICS risk so they can ask the right questions,” stated Dan Shugrue, CyberX's senior director of industrial cybersecurity. “We’re definitely making progress in reducing ICS risk, but we have a long way to go. Reducing ICS risk is a journey — most of these ICS networks were designed decades ago, long before cybersecurity was a key design priority.”

 14 DAY TRIAL //
14 DAY TRIAL //