Researchers from Cisco Talos Intelligence Group have uncovered even more capabilities of the highly sophisticated multi-stage malware platform VPNFilter, making it one of the few known malicious frameworks of this complexity.
As detailed in their report, Talos Intelligence has been researching VPNFilter for months since its initial discovery at the beginning of 2018 when the malware was estimated to have infected at least 500K devices from 54 countries around the globe at its peak.
In their initial report, the security researchers said that VPNFilter was capable of compromising a massive range of Internet-connected devices, from MikroTik, Linksys, NETGEAR, and TP-Link routers to QNAP network-attached storage (NAS) devices.
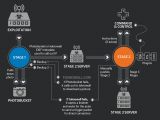
VPNFilter is known to be a multi-stage threat, with the first stage being persistent through reboots and ready to deploy the second stage designed to collect and exfiltrate data, as well as execute malicious commands and manage infected devices.
The second stage also comes with destructive capabilities which allows it to brick infected devices by partially overwriting the firmware.
VPNFilter's long list of capabilities makes it one of if not the most dangerous malware frameworks known to scour the Internet for vulnerable devices
VPNFilter's third stage is comprised of plugins designed to expand the capabilities of the second stage, with packet sniffing capabilities, TOR communication, exploit delivery to compromised devices via JavaScript injection, and some extra abilities for the second stage destruction module which allows it to system files.
Talos Intelligence's last report details new third stage modules known to add extra exploiting skills, data filtering, and encrypted tunneling for hiding data exfiltration and C&C communication traffic.
Furthermore, according to the new analysis, VPNFilter also has modules capable of identifying new exploitable targets within the same network or in other networks the threat actors want to target and for adding infected devices to a proxy network for attack obfuscation.
The highly versatile malware is also now known of being able to create network maps, allow its masters to connect through SSH, to exploit endpoints through executable injection, to forward ports, to create SOCKS5 proxies, and to take part in coordinated denial-of-service attacks.
Thankfully, according to the Talos Intelligence researchers, VPNFilter seems to have been fully neutralized but, given the skills of the threat actors who created this multi-stage all-encompassing malware platform, it's hard to know for sure what their future intentions are.

 14 DAY TRIAL //
14 DAY TRIAL //