A new threat group named GreyEnergy by the security researchers at ESET has been unmasked as the most probable successor of BlackEnergy, an APT group which was behind the first ever witnessed blackout in 2015 caused by a cyber attack in Ukraine.
According to ESET's analysis of the new cyber-espionage group's behavior and toolkit, they have been targeting a multitude of targets across Europe, focusing on industrial control systems known to be part of critical infrastructure.
Furthermore, GreyEnergy "mirrors and improves upon already-sophisticated techniques used in the Ukraine power grid outages and has the potential to spread worldwide."
ESET first managed to find traces of GreyEnergy's malware toolkit used during attacks on a Polish energy company in 2015 while BlackEnergy was still active and right before it caused the Ukrainian cyber attack-based blackout which affected around 230,000 people.
Additionally, GreyEnergy was also found to be behind the initial deployment of a NotPetya predecessor (dubbed Moonraker Petya) which, in turn, was a variant of the Petya ransomware with the added capability of propagating using the NSA-leaked EternalBlue exploit.
Although the actors behind GreyEnergy did their best to stay unnoticed since their first appearance in 2015, the threat group's malware toolkit was also observed in action during attacks on multiple Ukrainian targets.
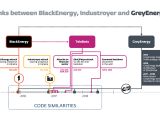
GreyEnergy's infiltration techniques are similar to the ones used by BlackEnergy, but with a more modern toolkit and a focus on stealthiness
"GreyEnergy’s malware framework bears many similarities to BlackEnergy, as outlined below. It is similarly modular in construction, so its functionality is dependent on the particular combination of modules its operator uploads to each of the targeted victim systems," ESET points out.
Moreover, GreyEnergy is capable of deploying malware modules designed to perform a wide range of tasks from data exfiltration and keylogging to installing backdoors and stealing credentials.
Although the GreyEnergy APT group has not yet been observed to directly attack Industrial Control Systems (ICS) they have been witnessed attacking SCADA servers and software which run on ICS stations, components designed to run around the clock because they are connected to mission-critical systems.
Unlike BlackEnergy, the new threat group makes use of more modern tools focused on stealthiness and it deploys fileless (in-memory) malware modules on targeted machines to make detection as hard as possible.
GreyEnergy has also been connected to the TeleBots threat subgroup, the actors behind the DiskCoder.C ransomware outbreak, with core code from Moonraker Petya being reused to develop the NotPetya worm.
A full description of the newly uncovered APT group GreyEnergy is available in ESET's GreyEnergy: A successor to BlackEnergy whitepaper and a list of all related Indicators of Compromise (IoC) is available on the "GreyEnergy — Indicators of Compromise" GitHub page.

 14 DAY TRIAL //
14 DAY TRIAL //