- By Eduard Kovacs
- July 3rd, 2013

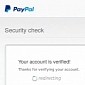
Fake Pinterest Password Change Notifications Lure Users to BlackHole Websites
The malicious websites are set up to serve a version of the Cridex malware
- By Eduard Kovacs
- July 3rd, 2013
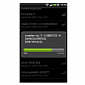
Fake Wi-Fi Password Hacker App Identified on Amazon Appstore for Android
Symantec experts say the application is designed to push advertisements
- By Eduard Kovacs
- July 3rd, 2013

Tens of Organizations Impacted by Vendini Data Breach
Around 30 organizations have been affected so far, but the number could be much higher
- By Eduard Kovacs
- July 3rd, 2013
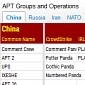
Government, Telecom and Energy Sectors in the Middle East Targeted with njRAT
Fidelis Security Systems researchers have analyzed the threat
- By Eduard Kovacs
- July 3rd, 2013
US Air Force Culture and Language Center Site Taken Down After Being Hacked
Turkish Ajan hackers have leaked a lot of sensitive data
- By Eduard Kovacs
- July 3rd, 2013

Pakistan’s Quaid-i-Azam University Breached by Indian Hacker, Data Leaked
The university's systems have been hacked for the second time in less than a month
- By Eduard Kovacs
- July 3rd, 2013
Turkey’s Directorate of Religious Affairs Hacked by RedHack
The attack was launched in protest against the Sivas massacre that took place 20 years ago
- By Eduard Kovacs
- July 3rd, 2013

Following Public Comments, FTC Approves Final Order to Settle Charges Against HTC
HTC must address security holes in the development phase
- By Eduard Kovacs
- July 2nd, 2013

Commander Cliff Neve Appointed as VP of Security Services at MAD Security
Neve previously worked as chief of operations for Coast Guard Cyber Command
- By Eduard Kovacs
- July 2nd, 2013

Help NIST Speed Up Responses of Computer Incident Teams
Submit your ideas for a new CSIRT guide by July 29, 2013
- By Eduard Kovacs
- July 2nd, 2013

Incapsula Launches Two-Factor Authentication for Websites
Login Protect can be enabled instantly without the need for application changes
- By Eduard Kovacs
- July 2nd, 2013

Play Panda Security’s Space Invaders on Facebook and Win an iPad Mini
In case you want a free iPad, but you're tired of all the scam offers
- By Eduard Kovacs
- July 2nd, 2013
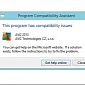
AVG 2013 Fully Compatible with Windows 8.1, Company Says
In rare cases, the Program Compatibility Assistant might detect some issues
- By Eduard Kovacs
- July 2nd, 2013
![Britain's Networks Hit by 70 Sophisticated Cyber Espionage Operations per Month [BBC] Britain's Networks Hit by 70 Sophisticated Cyber Espionage Operations per Month [BBC]](https://news-cdn.softpedia.com/images/news2/Britain-s-Networks-Hit-by-70-Sophisticated-Cyber-Espionage-Operations-Per-Month-BBC-1.png)
Britain's Networks Hit by 70 Sophisticated Cyber Espionage Operations per Month [BBC]
Officials say they know who is launching the attacks
- By Eduard Kovacs
- July 2nd, 2013
Experts Identify Trojan Designed to Steal Litecoin Wallets
The threat steals wallet.dat files and uploads them to an FTP server
- By Eduard Kovacs
- July 2nd, 2013

Indian Government Releases National Cyber Security Policy 2013
The National Security Council Secretariat will coordinate cyber security-related matters
- By Eduard Kovacs
- July 2nd, 2013

Atlassian Unable to Confirm Existence of Unpatched Backdoor in Crowd
The company says it hasn't been contacted by Command Five