UK security researcher Henry Hoggard has found a very simple method of bypassing PayPal's two-factor authentication (2FA) mechanism, allowing an attacker to take over PayPal accounts in less than a minute.
The researcher claims to have discovered this method while in a hotel with no telephone signal, and no way to receive the 2FA verification code to his device via SMS.
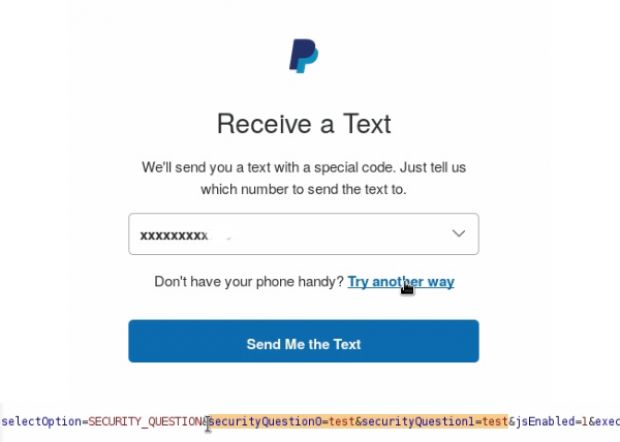
The researcher says the problem was found in the "Try another way" link that appears under the 2FA section of the login screen. PayPal provides this option to PayPal account owners for situations when they can't reach their phone, or they have no signal, as was case for him.
In this type of situations, PayPal asks the user to answer his security questions.
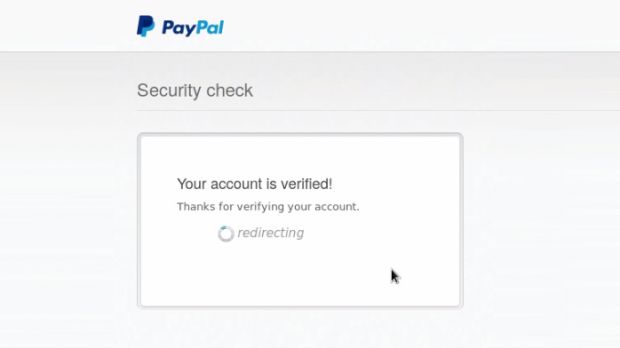
Hoggard discovered that if the attacker had a proxy server running that can intercept and hold the PayPal server requests, it would allow him to tamper with the HTTP data and trick PayPal into granting him access to the account.
All the attacker had to do was to remove the "securityQuestion0" and "securityQuestion1" parameters from the HTTP request, as seen below.
The technical skills needed to carry out such attacks are entry level for any hacker wannabe.
Hoggard reported the issue to PayPal on October 3, and engineers removed the authentication loophole by October 21.
 14 DAY TRIAL //
14 DAY TRIAL //