Cyber-espionage is one of the strangest trends in infosec today because even if most people don't understand what's going on, who's attacking whom, and why it is important, they flock to these reports like to a Katty Perry concert.
Making sense of all the malware nicknames, APT names, and finding out the country behind a cyber-espionage campaign can get on your nerves really quickly.
Does the Turla Group mean anything to you? Is it a cyber-espionage campaign backed up by Russia or China? Or is it Iran? Did they use malware X, malware Y, or malware Z? How many operations did they run? When was the latest? Where can you find the reports? Do other cyber-security firms use the same name, or do they have alternative nicknames?
All of these are common questions for both venerable infosec experts and some of our readers.
In the past, there were some projects, like APTNotes, Cyber Campaigns, and a few others, that tried to put all of these in order.
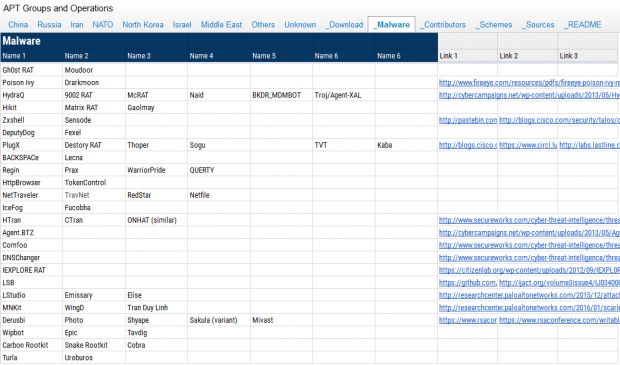
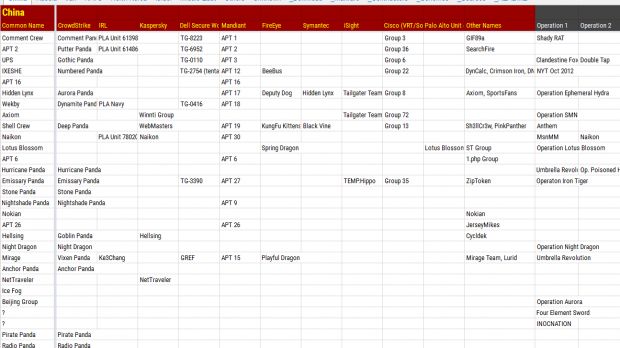
But there's now an even better source, organized into a nice and colorful spreadsheet hosted on Google Docs, named APT Groups and Operations.
The spreadsheet was put together by Florian Roth - @cyb3rops, but we did stumble upon it via Krypt3ia's blog (so thanks, Krypt3ia). If you ever want to become an infosec ninja, learn it by heart.
 14 DAY TRIAL //
14 DAY TRIAL //