- Security
- By Ionut Ilascu
- June 23rd, 2015
Winnti Malware Gets into Pharmaceutical Business
Operators sign rootkit with stolen certificate
- Security
- By Ionut Ilascu
- January 30th, 2015

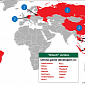
Skeleton Key Malware Active for Two Years
Threat actors use it with Winnti to compromise networks
- Security Blog
- By Eduard Kovacs
- May 10th, 2013
Winnti Backdoor Created with Aheadlib to Mimic Legitimate System Library
Trend Micro experts have analyzed this interesting threat