A large pharmaceutical company in Europe has been targeted by the operators of Winnti, a piece of malware believed to be used to exfiltrate sensitive information from entities related to the gaming business.
Winnti was first spotted by Kaspersky in 2012, and samples of the malware were seen used by threat actor Axiom Group, whose actions were thwarted in 2014 during Operation SMN, which involved multiple security firms led by Novetta, a company offering advanced analytics solutions.
Campaign ID uses name of prominent pharmaceutical company
“For a long time the Winnti group had been considered as a Chinese threat actor targeting gaming companies specifically,” said Dmitry Tarakanov of Kaspersky in a blog post on Monday.
However, recent findings show that the campaigns of the Winnti group target entities from a wider range of sectors, as Kaspersky picked up samples from the toolkit version analyzed by Novetta that suggested an attack on a “well-known global pharmaceutical company headquartered in Europe.”
The researchers did not name the victim, but according to Wikipedia, six of the top ten companies ranked by revenue as per their 2013 annual reports are from Europe: Roche, GlaxoSmithKline, Novartis, Sanofi, AstraZeneca, and Bayer.
Apart from the campaign ID, the researchers found other clues supporting cyber-espionage activity focused on the pharmaceutical industry. The analyzed Winnti sample included a network rootkit signed with a stolen certificate assigned to a division of a large Japanese holding that is involved in the development and production of drugs and medical equipment.
Winnti is used against targets from different sectors
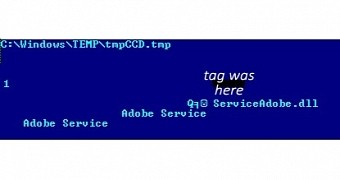
Indication that Winnti has compromised a computer system is the presence of “tmpCCD.tmp” in the Windows temporary folder and the files “ServiceAdobe.dll” and “ksadobe.dat.” When working, the RAT (remote access Trojan) also uses a service pretending to be from Adobe (Adobe Service).
The level of involvement of Winnti operators in cyber-espionage operations has yet to be determined, but it is clear that the malware has been adopted for activities that go beyond the online gaming development sector.
Tarakanov says that whenever Winnti is mentioned, it should be assumed that the list of targets includes at least telecommunication and large pharmaceutical companies.
 14 DAY TRIAL //
14 DAY TRIAL //