- Virus alerts
- By Catalin Cimpanu
- July 4th, 2016
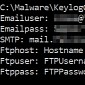
HawkEye Keylogger Users Employ Hacked Emails Accounts to Receive Stolen Data
They also leverage RTF exploits to infect users
- Security
- By Lucian Constantin
- May 5th, 2011

US Government Departments Targeted in bin Laden Death-Themed Attack
- Security
- By Lucian Constantin
- December 15th, 2010
