Crooks using the HawkEye keylogger are employing hacked email accounts to reroute data stolen from infected systems to the attacker's email address.
Security researchers from Trustwave have discovered a spam email campaign delivering malicious RTF documents masquerading as Word files.
HawkEye keylogger campaign leverages 2 RTF exploits
These files used the CVE-2010-3333 Office exploit, sometimes CVE-2012-0158, to infect recipients with the HawkEye keylogger, a malicious application sold on the public Internet.
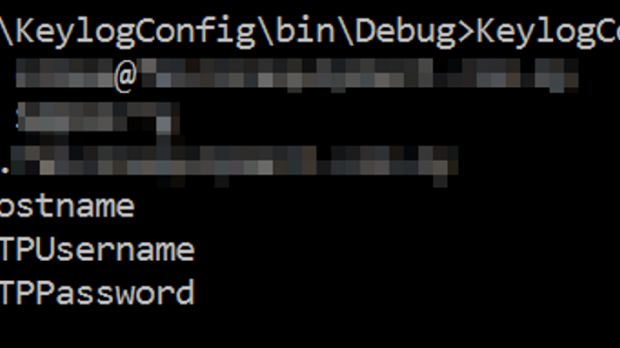
HawkEye is a dangerous threat, coming with lots of features that allow crooks to collect email, browser, and FTP settings and passwords.
This keylogger enables people to buy a copy, infect users, collect their data and then receive it in the form of an email, FTP data transfer, or upload to a PHP website.
Trustwave researchers said that, after they reverse-engineered a copy of the HawkEye keylogger, they discovered in one of its configuration files the email address and password for the account to where the keylogger was sending all the stolen data.
Odd choice to use actual email accounts instead of dummy inboxes
Using these credentials, the security researchers logged into the email account, and to their surprise, this wasn't just a dummy account but belonged to a real person.
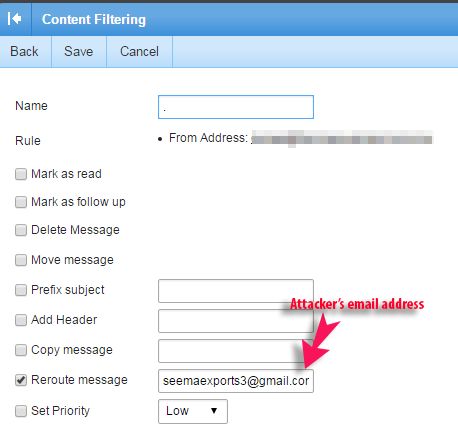
"Perhaps the attacker knows that the HawkEye keylogger can be easily cracked, and to protect their own email credentials, they've hijacked a compromised email account as the initial receiver that eventually forward emails to the attacker's own email address," Trustwave's Rodel Mendrez says.
The hijacked account included a rule that was rerouting all messages received from a specific victim's email address to the attacker's own inbox.
By not leaving his own account password in the keylogger settings, the author was avoiding having his operations taken over by security researchers.
It is odd that he would use a hijacked email account instead of a dummy inbox, which would have reduced the chance of being discovered even more.
 14 DAY TRIAL //
14 DAY TRIAL //