After news of the death of Angler and Nuclear, two of today's most popular exploit kits came out, security firm Zscaler has kept an eye on their competition, the Sundown Exploit Kit (EK).
Over a three-week period from June 15 to July 7, the company's security experts saw a surge of activity as the crooks behind this crime kit were trying to update their malicious code to make their product more appealing to cyber-criminals looking for an Angler or Nuclear alternative.
While the Neutrino and RIG exploit kits filled most of the market gap, Sundown is definitely giving the Magnitude EK a run for its money for the number three position.
Zscaler researchers claim that, in the period they kept an eye on the activity from Sundown deployments, they saw its creators frantically pushing new updates and tricks almost every few days, to make their product more appealing to potential customers.
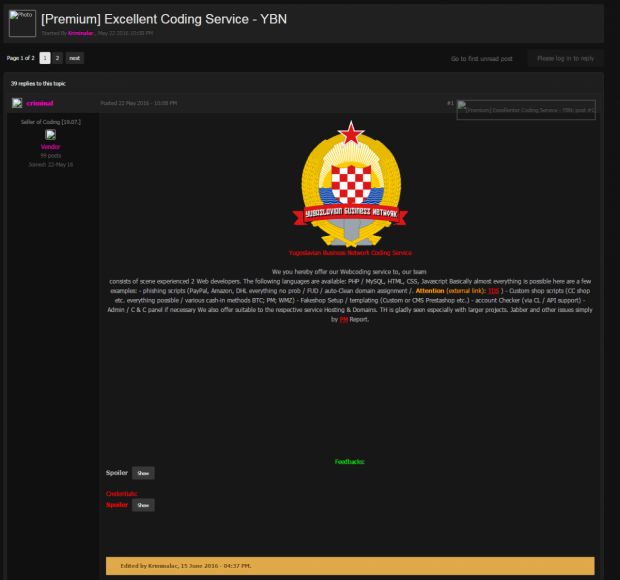
Further, in their probing, the company's experts discovered clues that may tie the EK's activity to a group of cyber-criminals called YBN, or the Yugoslavian Bussiness Network, akin the famous RBN - Russian Business Network.
"This Russian Business Network inspired group may or may not be responsible for Sundown, but there does appear to be a German language group offering coding services on forums under the YBN moniker, with many commenters voicing their pleasure with the services," Zscaler researcher Ed Miles writes in the company's report.

 14 DAY TRIAL //
14 DAY TRIAL //