Angler, the world's most popular exploit kit, appears to have shut down, as cyber-criminals are moving their operations to other exploits kits such as Neutrino, RIG, and Sundown, according to a tip received by Softpedia from Jerome Segura of Malwarebytes.
If this is the first time you read about an exploit kit such as Angler, these are specialized Web-based applications that sit on a website and await visitors. Crooks use malvertising attacks, hidden redirections on hacked sites, or spam campaigns to send traffic to these Web pages.
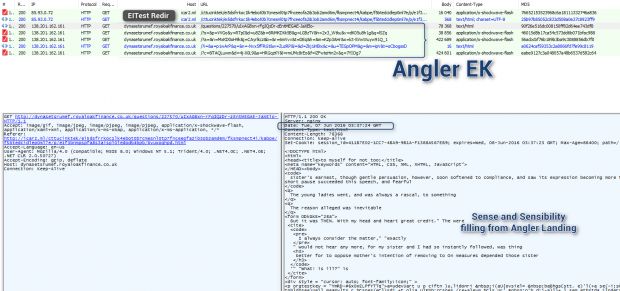
Here, exploit kits (EKs) like Angler test the user's locally installed software and detect vulnerable versions. They then deliver malicious code via JavaScript, Flash, or Silverlight that exploits these weaknesses in order to download and installs malware in what's known as a drive-by download. Most users never notice anything, unless they have antivirus software installed on their computers.
Top malvertising actors have already switched to the Neutrino EK
Mr. Segura, whose company is an expert on malvertising campaigns and exploit kit usage, has been blogging lately about multiple cyber-crime operations that have started switching away from the Angler Exploit Kit (EK).
The same things have also been reported by a security researcher named Kaffeine (Malware don't need Coffee blog) and Brad Duncan (Malware Traffic Analysis blog).
All three say that important actors in the malvertising scene are now migrating to other exploit kits, but mainly Neutrino.
"The changes we saw are profound," Segura told Softpedia. "Some actors only ever worked with Angler, esp. those top malvertising campaigns."
Long-time Angler fans have moved as well
Researcher Kaffeine notes that while Angler has had ups and downs in terms of activity, it has also had periods of downtime, usually when the people behind the exploit kit went on vacations or performed server maintenance.
GooNky, the name of one of the biggest malvertising actors, even synchronized its periods of inactivity with Angler's. The most recent one was in January 2016, when both groups took a break and returned at the same time.
Now, even long-time fan GooNky has switched to the Neutrino EK, one of Angler's competitors, along with SadClowns, another major player on the malvertising market.
Neutrino doubles rental price to take advantage of Angler's disappearance
As for Angler's rivals, Kaffeine says that Neutrino just doubled its price on the underground market, going from $3,500 per month to $7,000, while also dropping the weekly rental option.
It appears that Angler's rivals are trying to capitalize on the void created on the market after Angler's apparent disappearance. This is somewhat reminiscent of the way Neutrino's authors reacted after the author of the Blackhole exploit kit was arrested in 2013.
At the start of June, Russian authorities announced their largest cybercrime bust in history, during which they arrested 50 people and detained 18.
Russian authorities revealed that the crooks they arrested were involved in the creation of the Lurk trojan. Kaffeine says that, between 2012 and the start of 2016, the Lurk trojan was distributed via the Angler EK.
Malwarebytes, Kaffeine, and Brad Duncan report that the last instance of the Angler EK used in a live malvertising campaign was recorded on June 7. Previously, the Nuclear EK also disappeared without a trace around April 30.
UPDATE [June 13, 2016]: A tweet from F-Secure comes to confirm the findings of the other three researchers.
UPDATE [June 14, 2016]: Forcepoint security researchers have now observed the same thing, seing the last Angler activity on June 9, 2016.
UPDATE [June 17, 2016]: A Proofpoint report also reaches the same conclusion on Angler's potential demise.
Our exploit kit stats for the last two weeks… Angler dives, Neutrino soars. pic.twitter.com/RcYAH6tVck — News from the Lab (@FSLabs) June 13, 2016

 14 DAY TRIAL //
14 DAY TRIAL //