A 7-year-old advanced persistent threat (APT) group known under different names has made a comeback this year, employing new tools to infiltrate high-profile targets like governments and defense contractors, reports Kaspersky Labs' GReAT (Global Research and Analysis Team) division.
APT28, Sofacy, Fancy Bear, Sednit, or Strontium are all names given to this group by various cyber-security vendors that have analyzed their operations. The most recent of them is Microsoft, who included them as the featured threat in their recent Security Intelligence Report Volume 19 report.
Sofacy now uses double-headed backdoors
Today, Kaspersky is shedding more light on this group's operations, revealing some of the tools and techniques they've used against a defense contractor in the course of August this year.
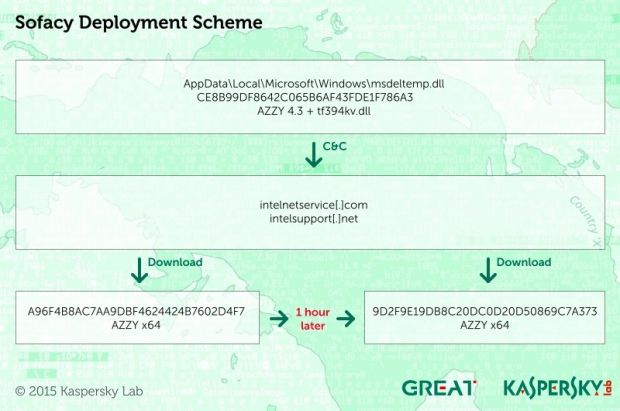
Sofacy, as Kaspersky calls them, diversified its hacking arsenal this year with the addition of a set of more complex backdoors (AZZY family), all interchangeable and used together, one as a fallback in case the others don't manage to get a foothold on targeted systems.
Additionally, attackers also employed modularization techniques when putting together their malware, and now pack only the bare minimum in each threat, loading more code via modules sent from the C&C server when system scans on infected targets show vulnerable software ready to be exploited.
This technique was used for the backdoors themselves, as Kaspersky staff explains: "Separating C&C communications functions from the main backdoor is also a way of decreasing visibility of the main backdoor."
"As it doesn’t directly transmit data outside the attacked computer, it looks less suspicious from a security point of view," said Kaspersky, referring to the fact that Sofacy employed side-loaded DLLs to hide the backdoor's location and communicate with the C&C server.
Sofacy developed a new infostealer targeting USB storage devices
Furthermore, the group also used a new infostealer targeting USBs, dubbed USBSTEALER, malware that watches removable drives, secretly stealing and exfiltrating data whenever new devices are connected to an infected PC.
All stolen data is stored in a hidden directory on infected computers and sent through the AZZY backdoors to Sofacy's servers.
USBSTEALER was first seen in February 2015 and was used only on high-profile targets.
All initial Sofacy infections relied on six zero-day exploits in Microsoft Office, Oracle Sun Java, Adobe Flash Player and Windows itself.

 14 DAY TRIAL //
14 DAY TRIAL //