Earlier this year, various security vendors have published their investigations into a Russian advanced persistence threat (APT) group known under different names: APT28, Sofacy, Fancy Bear, Sednit, or the most common one, Operation Pawn Storm.
In Microsoft's recent Security Intelligence Report, the Redmond-giant has revealed its own team's analysis of this APT, with data it gathered from clients it's protecting through its security products. The code given by Microsoft to this APT is Strontium.
According to Microsoft security team's analysis, Strontium, since its first sighting back in 2007, has targeted individuals from government bodies, the military (especially NATO forces), diplomats, journalists, and other political figures.
The security researchers took notice of the group after earlier this year its members started using Microsoft-themed spear phishing campaigns to trick victims into revealing sensitive Outlook credentials.
Besides abusing Microsoft's brand to mislead users, Strontium has also been observed sending spear phishing emails just before conferences, but also malicious links via social media.
Strontium, a state-sponsored actor, with a taste for military and government targets
Microsoft's analysis shows that these are not ordinary criminals sending out spam to a large number of users. Strontium operators target a very small number of individuals, and based on the level of details they embed in each new spear phishing campaign, Microsoft believes it is a state-sponsored group.
This confirms and comes in line with other conclusions that other security vendors have provided.
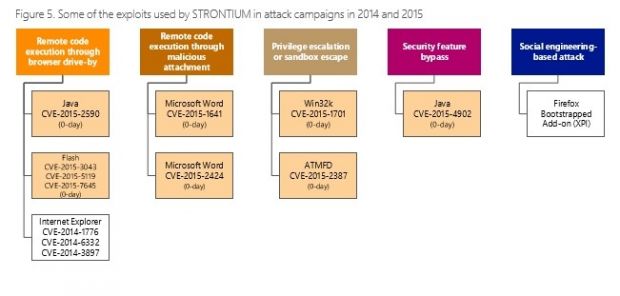
Additionally, Microsoft also reveals a slew of very sophisticated zero-day vulnerabilities the group is using, in products like Flash, Java, Microsoft Word, and Internet Explorer.
The Redmond-based company recommends that enterprises implement 2FA (2-Factor Authentication) as quick as possible, to reduce the risk of employees falling to classic spear phishing tactics, the group's favorite entry point for infecting victims and taking advantage of its powerful zero-day bugs arsenal.
More in-depth details about the Strontium group, along with other Microsoft-related security news can be read in Microsoft Security Intelligence Report Volume 19 report.

 14 DAY TRIAL //
14 DAY TRIAL //