The practice of hacking malware botnets and then replacing their payloads with pro-user content is starting to become the norm, with another of these incidents being reported by the team from F-Secure.
The company says that one of its security researchers stumbled upon a weird sample coming from the server network (botnet) from which most of the Locky ransomware-carrying spam is sent out.
The file was a ZIP archive containing a JavaScript file. If the user double-clicked this JavaScript file, the script would download in normal circumstances the Locky ransomware and launch it into execution, effectively encrypting their files.
This time around, the F-Secure researcher, named Päivi T., discovered that, instead of Locky, this file was downloading something different, also launching it into execution.
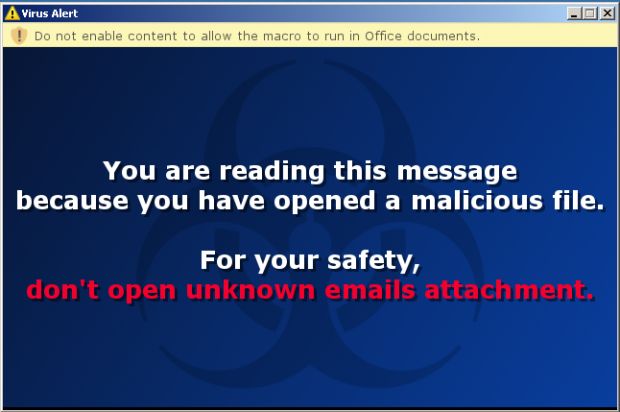
It appears that someone hacked the Locky distribution network and replaced the Locky ransomware payload with a benign file that showed a simple popup warning users not to open email attachments from untrusted sources (screenshot below).
"You are reading this message because you have opened a malicious file," the popup reads. "For your safety, don't open unknown emails attachment."[sic]
Something like this happened before last February, when somebody hacked the Dridex botnet to deliver a version of the Avira antivirus installer instead of the Dridex banking trojan, and then again last month with the Locky network, when someone replaced the ransomware with an empty file that read "STUPID LOCKY."

 14 DAY TRIAL //
14 DAY TRIAL //