- Security
- By Gabriela Vatu
- April 24th, 2017

New Locky Ransomware Campaign Detected, Spreading via Spam Emails
Locky ransomware is back with a new spam campaign
- Virus alerts
- By Catalin Cimpanu
- October 27th, 2016

Hungarian Developer Most Likely Behind Hucky Ransomware
New Locky clone discovered by Avast researchers
- Virus alerts
- By Catalin Cimpanu
- October 24th, 2016
Locky Adds Support for a New "S**T" Extension
New spam campaign has made victims all over the world
- Security
- By Catalin Cimpanu
- October 23rd, 2016

Ransomware Reaches the Malware Top 3 for the First Time
Locky enters the Top 10 most prevalent malware standings
- Spam Reports
- By Catalin Cimpanu
- October 20th, 2016

Locky Spam Numbers Go Down as Ransomware Switches to LNK Files
Locky group changes spam & infection technique
- Spam Reports
- By Catalin Cimpanu
- October 16th, 2016
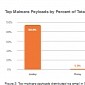
Locky Ransomware Accounted for 97 Percent of All Malicious Email Attachments
Exploit kit activity slows down dramatically
- Virus alerts
- By Catalin Cimpanu
- September 30th, 2016

Locky Drops Offline Mode and Switches to New ODIN Extension
Locky offline mode experiment seems to end as ransomware operators revert back to using online C&C servers
- Virus alerts
- By Catalin Cimpanu
- September 18th, 2016

Trojan Sold on Hacking Forum Ends Up in Locky Ransomware Distribution Chain
New trojan released on Russian hacking forums
- Virus alerts
- By Catalin Cimpanu
- August 26th, 2016

New Locky Ransomware Version Delivered as DLL File
Locky switches EXE binaries for DLL files
- Spam Reports
- By Catalin Cimpanu
- August 20th, 2016

Dridex Returns with New Spam Campaign After Two-Month Hiatus
Dridex now focuses on high-value targets
- Spam Reports
- By Catalin Cimpanu
- August 18th, 2016

Locky Ransomware Spam Campaigns Switch to Macro-Based Distribution
Dridex spam distribution stops altogether
- Server related
- By Catalin Cimpanu
- August 12th, 2016

Locky Ransomware Uses Vulnerable PHP Forms for Spam Distribution
Updating the vulnerable PHP scripts solves the problem
- Security
- By Catalin Cimpanu
- August 7th, 2016
Security Researcher Tricks Tech Support Scammer Into Installing Locky Ransomware
Infosec researcher has fun at a crook's expense
- Security
- By Catalin Cimpanu
- July 30th, 2016

Major Cyber-Crime Campaign Switches from CryptXXX to Locky Ransomware
Gang also migrates from Angler EK to Neutrino EK
- Spam Reports
- By Catalin Cimpanu
- July 28th, 2016
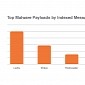
Locky Ransomware Was Top Malware Threat for Q2 2016
Q2 quieter than Q1 thanks to Angler and Nuclear shutdowns
- Virus alerts
- By Catalin Cimpanu
- July 26th, 2016

New Locky Spam Wave Delivers Entire Ransomware Inside JavaScript File
Locky ransomware continues to evolve, gets closer to 100% JS
- Spam Reports
- By Catalin Cimpanu
- July 14th, 2016

Huge Spam Wave Drops Locky Variant That Can Work Without an Internet Connection
New Locky variant uses a weaker encryption method