Malicious Office files used in five different cyber-espionage campaigns are linked by the same Office exploit kit, security researchers claim.
In June 2016, researchers from Palo Alto Networks discovered malicious Office files attached to spear-phishing emails received by an unnamed victim. The emails were spoofed to look like they came from the United Nations Environment Programme (UNEP).
HOMEKit exploit kit used to create malicious Office docs
Researchers tracked down these files to HOMEKit, a program used to inject malicious payloads inside the headers of Office documents.
This application, called an Office exploit kit, or just exploit kit, was used to insert malicious code that exploited the CVE-2012-0158 vulnerability, a weakness in how ActiveX controls are handled in Microsoft Office, to infect the underlying system with malware.
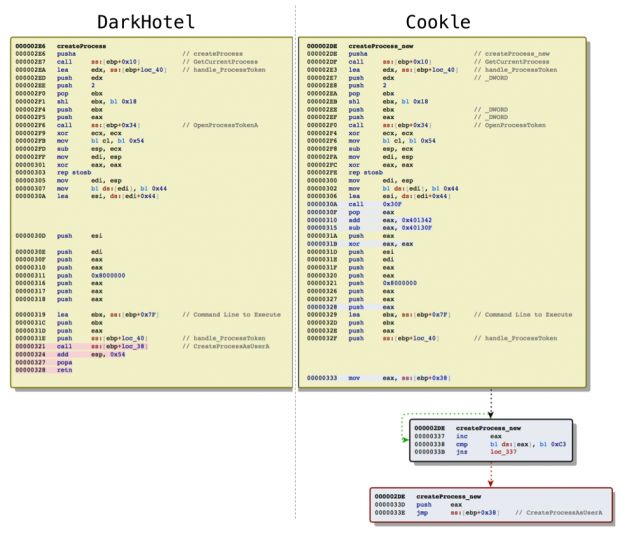
For this particular campaign, the crooks were using HOMEKit-generated malicious Word files to infect the recipient with Cookle, a malware dropper specialized in infecting targets and then downloading other more potent malware.
HOMEKit-generated files found in four other cyber-espionage campaigns
Researchers who analyzed these files found a pattern in how HOMEKit generates these malicious Office files.
Comparing the payload code appended to Office files, they managed to identify links to previous cyber-espionage campaigns detected since 2013 and after.
Based on the analyzed malware, researchers say that HOMEKit was used to create malicious Office files used to deliver the PlugX malware, a tool often associated with Chinese APTs. The same clues were found in the Surtr campaign against the Tibetan Chinese minority.
Additionally, similar Office payloads were found in the Mirage campaign, but also the infamous DarkHotel campaign that spied on foreign businessmen staying in hotels in various Asian countries. In fact, the researchers said the Cookle and DarkHotel payloads shared 90 percent of the exploit code.
"It is also possible that HOMEKit is a toolkit available to multiple threat actors, via a connected intermediary," the researchers presume. "Unfortunately, at this time, a lack of data does not allow us to come to a definitive answer."
A month earlier, Palo Alto also discovered another Office exploit kit called MNKit, which was used in various cyber-espionage operations as well.

 14 DAY TRIAL //
14 DAY TRIAL //