The highly complex backdoor malware payload designed by the GreyEnergy advanced persistent threat (APT) group is being dropped on targeted machines using the common phishing infection vector as detailed by Nozomi Networks' Alessandro Di Pinto.
GreyEnergy attacked and infiltrated the networks of multiple critical infrastructure targets from Eastern Europe, from Poland and Ukraine, with other objectives probably lined up for future attacks.
According to ESET, GreyEnergy is the most probable successor of the BlackEnergy cyber-espionage group, and it was found to be behind the original deployment of a NotPetya predecessor (dubbed Moonraker Petya), a variant of the Petya ransomware that comes with the extra capability of propagating using the NSA EternalBlue exploit.
Furthermore, even though GreyEnergy did its best to stay unnoticed since their first appearance in 2015, the threat group's malware toolkit was observed in action during attacks targeting multiple Ukrainian networks.
As discovered by Di Pinto, GreyEnergy attacks start with ordinary spear-phishing campaigns which use maliciously crafted Word documents designed to target specific people in the organization the APT group wants to infiltrate.
The document is written in Ukrainian, and it comes with the well-known macro warnings all such malicious files will display when opened. The threat group circumvents this issue by requesting the user to click the "Enable Content" button within the warning message if they want to interact with the document's content.
Greyenergy's malware toolkit uses P2P-based botnet communication to lower the risk of detection
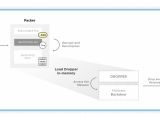
Once the button is clicked, the GreyEnergy malware code is extracted using the oledump tool and then goes straight to downloading and loading a packed dropper module in the system memory, which in turn is used during the next infection stage to drop the final persistent backdoor.
The backdoor will be dropped within the %APPDATA%/Microsoft/ folder and will use a name composed out of a random GUID and a .db extension to trick any potential victims that the backdoor binary is a safe database file.
The next steps in the multi-stage infection process make sure the backdoor achieves persistence by adding it to the Window Startup folder and launching it on the compromised system.
GreyEnergy's backdoor malware has a modular architecture which allows the APT group to quickly expand its capabilities and tailor it for each target, making it easy to add data collection, keylogging, and file system interaction abilities.
The infected machines are also added to a peer-to-peer network designed to allow for quick inter-communication between all the targets infiltrated by GreyEnergy and lowering the risk of detection by using a single bot to communicate with the command-and-control servers.
Although GreyEnergy used this malware toolkit only in cyberespionage campaigns impacting SCADA servers and ICS stations software, it's quite evident given the high-level skills demonstrated by the APT group that it can always upgrade it to infect Industrial Control Systems (ICS) if needed.

 14 DAY TRIAL //
14 DAY TRIAL //