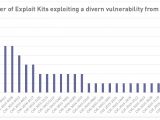
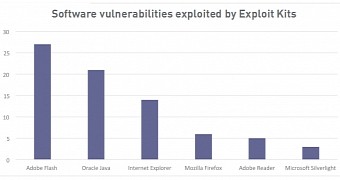
Exploit kit authors have a penchant for exploiting Flash issues, with 27 of the 76 vulnerabilities detected as part of exploit kit arsenals being Flash issues, some as old as 2013.
This finding is the result of a Digital Shadows study that analyzed all the 22 exploit kits active in the past years.
Only five exploit kits remain active
Researchers discovered that these exploit kits incorporated different vulnerabilities, mostly public and patched, all depending on the skill of the exploit kit's developer.
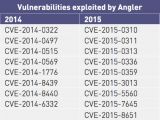
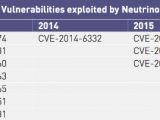
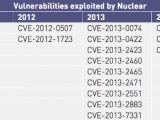
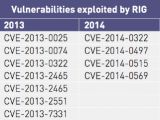
The study confirms once again that the most popular exploit kits were Angler (now defunct), Neutrino, Nuclear (now defunct), Magnitude, and RIG. Other popular exploit kits included Sundown, Hunter, Niteris, Hanjuan, and Fiesta.
Nevertheless, only a few of these exploit kits showed any activity in 2016. The only ones for which different security vendors detected active campaigns were Angler, Nuclear, Neutrino, Magnitude, RIG, Sundown, and Hunter, but two of these have ceased all activity, in April and June.
Flash is a popular targeted technology, but an IE bug reigns supreme
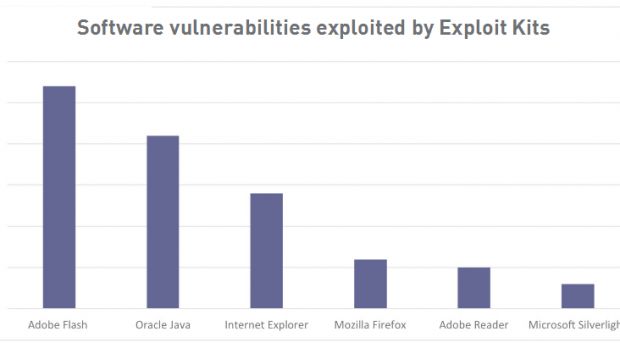
Researchers say that the most popular technology they found incorporated into exploit kits arsenals was Flash, with 27 of the total 76 vulnerabilities detected in live exploitation attempts.
Java was a close second, followed by other technologies and software such as Internet Explorer, Mozilla Firefox, Adobe Reader, and Microsoft Silverlight.
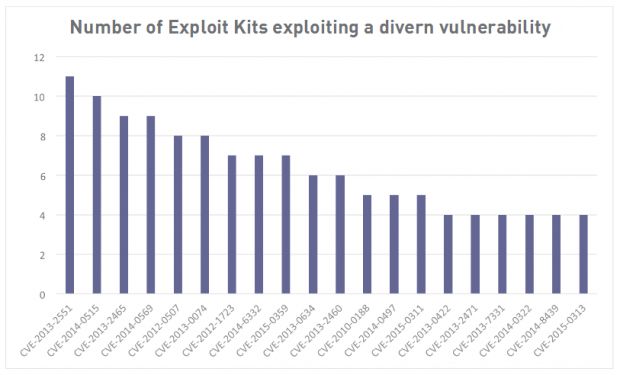
In spite of Flash's popularity, it is an Internet Explorer vulnerability that researchers said it was the most popular, used by half of all exploit kits in the past years.
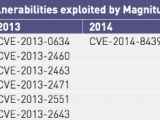
This was CVE-2013-2551, an issue affecting IE6 to IE10 that leads to remote code execution via a crafted website that triggers access to a deleted object, as demonstrated by VUPEN during a Pwn2Own competition at CanSecWest 2013.
The second most popular vulnerability was CVE-2014-0515 in Flash, and the third was a tie between CVE-2013-2465 in Java and CVE-2014-0569 in Flash.
Digital Shadow researchers also say that after taking a closer look at the exploit kit market, you can clearly see that, as technology moves forward, so do exploit kits, with many dropping support for older exploits and moving to vulnerabilities discovered after 2015.
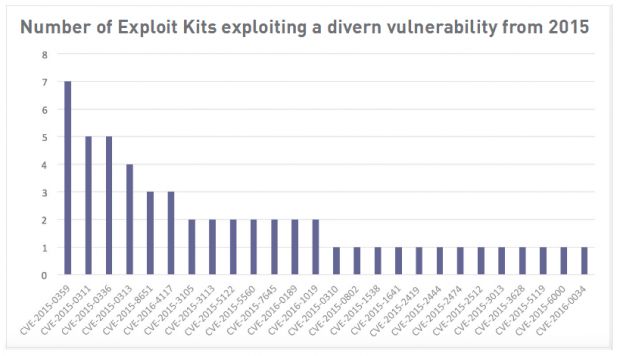
Flash - a targeted technology after 2015
Taking into account only vulnerabilities discovered after 2015, which might still be found in a very large number of active computers, researchers say that the top three most popular vulnerabilities are all in Flash. An explanation for this may also be found in Java and IE's sinking market share.
"While CVE-2013-2551 was the most shared of all the known vulnerabilities exploited, it is not known if this remains viable or present within exploit kits active at the time of writing," the Digital Shadows report reads.
"Furthermore, this vulnerability had been exploited by a number of kits for which we detected no activity in 2016. When coupled with it being an old vulnerability, this likely contributes to a decline in its exploitation," the security firm also adds.
"Conversely, more recent vulnerabilities, specifically those patched in 2015 and after, have a higher likelihood to remain actively exploited in the wild. Therefore, it is a realistic possibility that the top six vulnerabilities displayed in Figure 8 [see below] were the most frequently exploited at the time of writing."
 14 DAY TRIAL //
14 DAY TRIAL //