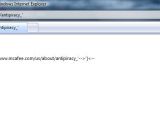
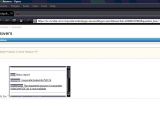
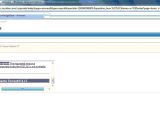
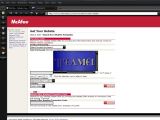
A self-confessed white-hat hacker has published proof-of-concept attacks against websites connected to global IT security vendor McAfee. XSS vulnerabilities allow for an IFrame injection and rogue redirection.
Methodman, a member of the Team Elite programming outfit, has published screenshots of the flaws he found in kc.mcafee.com and mcafeerebates.com, a website administered by a McAfee business partner. McAfee is just the latest addition to what begins to look like a long list of AV vendors, which includes names such as those of Symantec, Kaspersky, Avira, ESET, AVG, Bitdefender or F-Secure, whose websites have been found vulnerable to similar attacks.
Methodman also took credit for XSS flaws discovered in the websites of Intel, eBay and, more recently, the MPAA. The hacker ironically starts his post with a quote from the McAfee website, saying that, "We're driven to provide the broadest range of solutions, making it easy for our customers to secure their PCs, networks, mobile phones, and websites from emerging and known threats."
First, he documents a server XMLHTTP post request error on mcafee.com, then he moves on to the more interesting cross-site scripting bug in the KnowledgeBase section. As it is the case with most XSS flaws, this one is also caused by the poor input validation in a search form, allowing for arbitrary code to be injected into the page.
Attackers prefer leveraging on XSS flaws by injecting hidden IFrames into the page. The IFrames can, in turn, be used to load arbitrary content, such as exploits or malware, from external servers. Even though this is not a permanent XSS, malformed links can be created and spammed in malware-distribution campaigns, by combining them with other techniques in order to raise their credibility and trick more users.
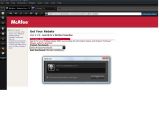
The mcafeerebates.com website has also been found to be vulnerable to a similar IFrame injection attack, but, in addition, its flaws can also be exploited to redirect visitors to any URL that the attacker desires or prompt rogue JavaScript alerts. Furthermore, while the weaknesses on the McAfee KnowledgeBase page have already been addressed by the time of writing this article, the ones on this third-party website were still active.
On a side note, the Romanian hacking outfit HackersBlog, which also specialized in finding vulnerabilities on the websites of AV vendors, prior to their retirement, have recently announced a possible comeback. A post on their website, which is currently in re-design mode, reads, "We'll be back very soon."

 14 DAY TRIAL //
14 DAY TRIAL //