The hackers' assault on security vendors' websites continues with ESET, developer of the popular NOD32 antivirus solution. Multiple websites controlled by the company are vulnerable to cross-site scripting and SQL injection.
A hacker calling himself Methodman has published proof-of-concept attacks against http://www.eset.com.tw, https://secure.eset.co.uk and http://www.virus-radar.com. The documented vulnerabilities can facilitate malware distribution, phishing campaigns, session cookies hijacking, as well as other attacks.
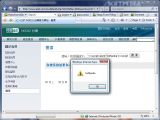
The XSS weaknesses on the Taiwanese website can be exploited to prompt arbitrary alerts, because of a search form that does not properly sanitize input. This behavior can be used to instrument attacks that employ social engineering techniques. In addition, through URL manipulation, the users lured into visiting the legit-looking website can be redirected to external pages controlled by the attackers.
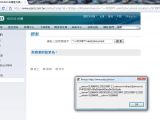
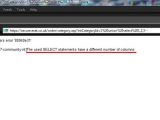
The SQL injection vulnerability on the UK website is rather interesting, because it is performed over HTTPS. According to the screenshots posted by Methodmad, the SQL injection reveals details about the ASP-coded website, which accesses a MySQL 5.0.27 database through an ODBC 3.51 driver.
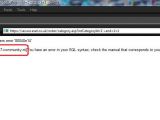
A poorly-sanitized input on a search form on the virus-radar.com website, which is used to publish statistics about e-mail threats, can also be used to force potentially-dangerous behavior. In addition to session cookie hijacking, arbitrary alert prompting and unauthorized redirection, the resulting cross-site scripting vulnerability also allows for rogue iframe injection.
Methodman has recently disclosed XSS vulnerabilities affecting the websites of other antivirus vendors as well, including Kaspersky and Avira. Of late, he has also reported that advisory pages on the Intel Product Security Center website can be misused by ill-intent attackers due to similar weaknesses.
The vulnerabilities on the ESET com.tw and co.uk websites were disclosed by the hacker on 22 February, 2008, and we contacted the AV vendor the next day, when we became aware of them. Unlike Avira and Kaspersky, ESET has not responded to our request for comment, but has fixed the flaws soon after we notified it.
The weakness on virus-radar.com has been published more recently and appears to be still active. Therefore, we have sent a secondary report to ESET along with a new inquiry into the matter. We're hoping that this time it will prove more responsive.
Update: We have been in contact over the weekend with Christopher Dale, ESET's Public Relations Manager, who kindly helped us obtain more information regarding this incident. According to Mr. Dale, the first notification we sent was not received by ESET for yet unknown reasons, nevertheless, the company "was first made aware of the problem on 22nd February."
The ESET representative pointed out that the websites affected by the vulnerabilities presented in this article were fully owned by independent distributors. However, he stressed that "ESET takes the security of our site and our partner sites very seriously."
The company's staff moved quickly to patch the disclosed flaws and it was noted that "while these types of attacks are very common on the Internet, they are addressed with the utmost urgency." In addition, ESET's investigation revealed that no sensitive customer information had been affected. "We have validated that our customer data resides in a separate location, and was never in danger of being compromised," Christopher Dale concluded.

 14 DAY TRIAL //
14 DAY TRIAL //