- Security Blog
- Hacking News
- Virus alerts
- Data Breaches
- Incidents
- Security Fixes and Improvements
- Spam Reports
- Advisories
- Server related
- Cyber Espionage
- Spyware Threats
- Weekly Roundup
- By Eduard Kovacs
- July 7th, 2012
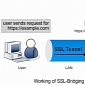
Cyberoam on DPI Device Vulnerability: Traffic Interception Is Not Possible
The company has explained the technology it uses for the HTTPS Deep Scan Inspection
- By Eduard Kovacs
- July 6th, 2012
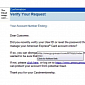
Blackhole Masters Ask American Express Users to Reset Passwords
It looks like a phishing campaign, but it's much worse than that
- By Eduard Kovacs
- July 6th, 2012

Court Rules in Favor of Fraud Victim, Blames Bank Security Systems
Ocean Bank held responsible after cybercriminals stole $588,000 (464,000 EUR) from firm
- By Eduard Kovacs
- July 6th, 2012

US Authorities Spread Fake Secrets to Identify Leakers
The Pentagon wants to make sure that no more information ends up on Wikileaks
- By Eduard Kovacs
- July 6th, 2012

Dutch ISP Finds That 120,000 of Its Customers Failed to Change Default Passwords
Anyone could have accessed the accounts to modify existing services
- By Eduard Kovacs
- July 6th, 2012

Torrent Sites Receive “We Are Anonymous” Messages Instead of Piracy Notices
The incident comes after India's anti-piracy outfit was breached by hacktivists
- By Eduard Kovacs
- July 6th, 2012
Security App of the Week: Secunia PSI 3.0
A great application that saves you the hassle of manually updating software
- By Eduard Kovacs
- July 6th, 2012
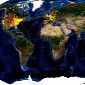
Tick Tock: It’s Lights Out for DNSChanger-Infected Computers on July 9 (Video)
Some ISPs will make sure that their customers will have Internet access even after Monday
- By Eduard Kovacs
- July 6th, 2012

Cybercriminals Recruit Money Mules by Sending Job Offer Emails
Some recruitment scams are more dangerous than others
- By Eduard Kovacs
- July 6th, 2012
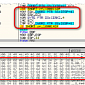
Monkif Botnet Avoids Detection by Receiving Commands Encrypted in JPEG Files
McAfee experts have analyzed the threat which seems to use the same server since 2009
- By Eduard Kovacs
- July 6th, 2012

13-Year-Old Arrested by Japanese Police for Creating Virus
He is also held responsible for operating a hacking discussion board
- By Eduard Kovacs
- July 6th, 2012

Hackers from Southeast Asia Breach India’s Central Bureau of Investigations
Luckily, the country's Cyber Defense Research Center was on guard
- By Eduard Kovacs
- July 6th, 2012
Controversy: Google Says Android Spam Botnet Does Not Exist
Some security researchers agree, but others still believe that malware is to blame
- By Eduard Kovacs
- July 5th, 2012

ICO 2011/12 Report: Monetary Penalties and Fight Against Illegal Marketing Calls
The fines issued by the organization add up to $3.1 million (2.5 million EUR)
- By Eduard Kovacs
- July 5th, 2012
Phonebook-Stealing Trojan Found on Apple App Store and Google Play (Updated)
The malware is designed to send SMS spam to all the numbers from the victim's contact list
- By Eduard Kovacs
- July 5th, 2012

“You Pig!” Emails Allegedly Containing Incriminating Pictures Spread Trojan
Never open an archive attached to an email, no matter how important it sounds
- By Eduard Kovacs
- July 5th, 2012
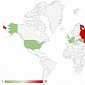
ENISA Warns Banks: Assume All PCs Are Infected
Operation High Roller caught the attention of the security agency