- By Eduard Kovacs
- August 16th, 2012
Bafruz Malware Replicates Antivirus Software in Order to Disable It, Microsoft Finds
Users can now remove the Trojan with the aid of the Malicious Software Removal Tool
- By Eduard Kovacs
- August 16th, 2012
Malicious "AntiHacker" Tool Installs DarkComet RAT to Spy on Syrian Activists
Supporters of the Syrian regime have once again launched a malicious operation
- By Eduard Kovacs
- August 14th, 2012
VPN Credentials of International Airport Employees Stolen by Trojan
Citadel's screen grabbing capabilities are put to good use
- By Eduard Kovacs
- August 10th, 2012

Tilon Trojan Relies on “Search and Replace” Mechanism to Alter Bank Websites
Tursteer experts identify a new version of the Silon malware
- By Eduard Kovacs
- August 10th, 2012

FBI on Reveton Ransomware: We Are Getting Dozens of Complaints Every Day
Some versions of the threat hijack the webcam to take pictures of the victim
- By Eduard Kovacs
- August 10th, 2012

Dorifel Malware Targets the Financial Details of Users from Netherlands
Kaspersky experts have found that the Trojan has already made over 3,000 victims
- By Eduard Kovacs
- August 9th, 2012
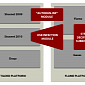
Gauss: State-Sponsored Banking Trojan Based on Flame Platform
Kaspersky experts detail a highly sophisticated piece of malware
- By Eduard Kovacs
- August 8th, 2012
Shylock Trojan Injects Attacker’s Phone Number into Bank Websites
The Shakespearean virus returns with an ace up its sleeve
- By Eduard Kovacs
- August 8th, 2012

F-Secure: 19 New Families of Android Malware Appeared in Q2 2012
The security firm's mobile threat report details the latest events and malicious elements
- By Eduard Kovacs
- August 7th, 2012
Mobile Version of ZeuS Trojan Targets BlackBerry Users
Four different samples have been identified by experts from Kaspersky
- By Ionut Arghire
- July 25th, 2012

New OSX/Crisis Trojan Found for Apple’s Mac Computers
It can install without user permissions, can hide itself
- By Eduard Kovacs
- July 19th, 2012

Good Guys Win: Grum, Third Largest Botnet in the World, Disrupted
The number of IPs used to send out spam dropped from 120,000 to 21,000 almost immediately
- By Eduard Kovacs
- July 18th, 2012

SMS, Email and Phone Call Floods Used by Fraudsters to Hide Illegal Money Transfers
An efficient way to ensure that banks can't confirm high value transactions
- By Eduard Kovacs
- July 18th, 2012

Madi Malware: Another Trojan Targets Organizations from the Middle East
Unlike Stuxnet and Flame, Madi relies on social engineering to infect computers
- By Eduard Kovacs
- July 17th, 2012

Dutch Authorities Take Down C&C Servers Used by Third Largest Spam Botnet
There’s less spam in the world after two of Grum’s servers have been taken down
- By Eduard Kovacs
- July 16th, 2012
Scareware Leverages Reputation of Industrial Espionage Malware
The scammers don’t know what Medre is or how to remove it
- By Eduard Kovacs
- July 12th, 2012
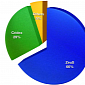
Experts: Phishing Campaigns Changed Since “Blackhole” Came into the Picture
Trend Micro experts published a detailed paper on spam runs that rely on the exploit kit