Kaspersky experts have released the details on Gauss, a dangerous piece of banking malware – deployed in August- September 2011 – which is capable of stealing sensitive information from infected Windows computers.
The threat, which is believed to be state-sponsored, comes with a mysterious encrypted payload that is activated only on certain system configurations.
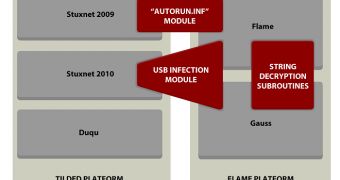
Developed sometime at the middle of 2011, Gauss has most likely been developed by the same group that’s behind the Flame malware.
The cyber-espionage toolkit supports new functions integrated into remotely deployable plugins. These plugins allow it to harvest system configurations, intercept browser cookies and passwords, infect USB drives, steal online banking credentials, hijack social media accounts, and list the content of system drives and folders.
At this point it’s still unknown how it spreads, but researchers haven’t discovered any self-spreading capabilities. One noteworthy observation is that is spreads more slowly than Flame.
While experts haven’t found Gauss to be utilizing any zero-day exploits, they have uncovered a “special payload” inside the malicious element.
“Gauss’ USB data stealing payload contains several encrypted sections which are decrypted with a key derived from certain system properties,” experts from Kaspersky’s Global Research & Analysis Team wrote.
“These sections are encrypted with an RC4 key derived from a MD5 hash performed 10000 times on a combination of a “%PATH%” environment string and the name of the directory in %PROGRAMFILES%. The RC4 key and the contents of these sections are not yet known - so we do not know the purpose of this hidden payload.”
Another thing that makes it stand out compared to other banking Trojans is the fact that it’s “fine-tuned” to target only particular financial institutions.
Over 2,500 victims have been identified, most of them residing in Lebanon (1,600), Israel, Palestine and Iran. A handful of infections have been seen in the US, UAE, Germany, Egypt, Qatar and Jordan.
Fortunately, this highly sophisticated malware’s spying capabilities have been put on standby in July 2012, when its command and control infrastructure was shut down.
Gauss has been identified as part of the effort initiated by the International Telecommunication Union.
A technical analysis made by Kaspersky on Gauss is available here.
 14 DAY TRIAL //
14 DAY TRIAL //