- By Eduard Kovacs
- September 11th, 2012

“Dangerous” Celebrities of 2012: Emma Watson, Jessica Biel and Eva Mendes
Search for them on Google and you'll most likely end up on a malware-laden site
- By Eduard Kovacs
- September 10th, 2012

Gaeilge Language Ransomware Targets Users from Ireland
Cybercriminals translate their messages to ensure the success of their campaigns
- By Eduard Kovacs
- August 31st, 2012
Java Zero-Day Leveraged in Nitro Campaign
The exploit was used in combination with Poison Ivy
- By Eduard Kovacs
- August 31st, 2012

Unknown Virus Disrupts World’s Second Largest Liquefied Natural Gas Company
The incident follows the attack on oil giant Saudi Aramco
- By Eduard Kovacs
- August 30th, 2012
Worm Spreads via Facebook, Skype, GTalk, MSN, Pidgin and ICQ
The malware can cause a lot of damage if an antivirus isn’t present
- By Eduard Kovacs
- August 29th, 2012

Researchers Unable to Link Mysterious Wiper Malware to Flame
There's not enough evidence to connect it to Duqu and Stuxnet either
- By Eduard Kovacs
- August 25th, 2012
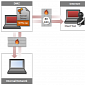
Cybercriminals Hijack Servers Remotely with Hikit APT
The attacker contacts the malware, not the other way around
- By Eduard Kovacs
- August 24th, 2012

Loozfon Android Malware Steals Contact Details from Female Users
The cybercriminals’ main purpose is to advertise a paid dating service
- By Eduard Kovacs
- August 23rd, 2012
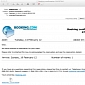
Androm Trojan Variant Comes in Fake Booking.com Emails
The company is warning customers to be on the lookout for such notifications
- By Eduard Kovacs
- August 22nd, 2012

Bogus Flash Player for Android Hides Adware and Trojans
Experts identified a number of sites which serve fake applications
- By Eduard Kovacs
- August 22nd, 2012
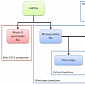
Crisis Spreads to Macs, Windows Computers, Mobile Devices and Virtual Machines
Researchers from Symantec analyze the new malware
- By Eduard Kovacs
- August 21st, 2012

Ransomware: Bad Guys, Good Guys and Untraceable Money Transfer Systems
ESET experts detail the way a ransomware scheme works
- By Eduard Kovacs
- August 21st, 2012

Adobe Flash Player Exploit Served Via “iPhone 5 Battery Images Leak” Emails
A harmless-looking document contains malicious .swf files
- By Eduard Kovacs
- August 20th, 2012
SMSZombie Trojan Exploits Vulnerability in China Mobile's Payment System
The malware has infected the devices of over 500,000 users
- By Eduard Kovacs
- August 17th, 2012
Shamoon Malware Covers Its Tracks by Wiping Master Boot Record
Experts from three different companies have analyzed the threat
- By Eduard Kovacs
- August 17th, 2012
MyAgent Trojan Targets Aerospace, Chemicals, Technology and Defense Industries
The malware uses a legitimate PDF document to mask its true purpose
- By Eduard Kovacs
- August 16th, 2012

Trojan Hides Its Payload by Using NTFS’s Extended Attributes Feature
The malware spreads as cracks and fake video codecs